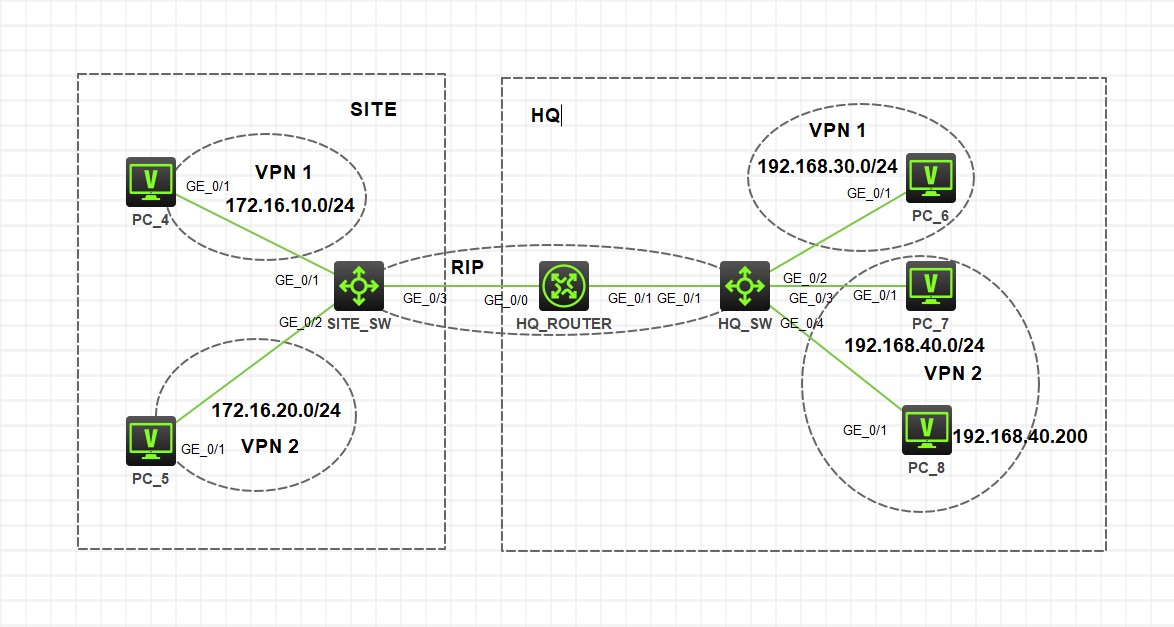
实验拓扑和需求
实验模拟的是一个总部和一个分支站点的网络,网络中总部和分支相同 VPN 实例网络互通,不同 VPN 实例网络相互隔离,总部 VPN2 中特殊主机 PC_8 需要访问位于分支网络中的 VPN1 网络
思路和解决方法
网络设备中配置 VPN instance 用来隔离不同网络数据
在不做特殊配置的情况下,不同 VPN 实例的网络是不能互相通信的
然而在设备上 VPN 实例引入其他 VPN 实例网络又会造成不同实例间网络能互通的情况,进而要做各种 ACL 限制
实验中并不涉及 MPLS VPN 的场景,有点类似 H3C 文档中 MCE 的情况,但是不涉及 CE、PE、RD、RT……
RD 是用来做路由区分的,RT 是 BGP 协议中团体属性的内容,本实验中都不涉及,本来也考虑使用 MPLS VPN 的方式做,但是就当前这个场景完全不需要,客户只需要把原有不同的几套网络隔离,还要考虑到设备特性,设备性能等等
实验中在路由经过的下一跳的设备上都要配置 VPN 实例,核心下联的二层设备不需要配置
由于不使用引入其他 VPN 实例的方式,需要在总部路由器和总部交换机上配置 VPN 静态路由
具体配置
SITE_SW
#
sysname SITE_SW
#
ip vpn-instance vpn1
#
ip vpn-instance vpn2
# 配置rip 100 绑定VPN1,宣告与总部互联的网络和分支VPN1的网络
rip 100 vpn-instance vpn1
undo summary
version 2
network 10.1.1.1 0.0.0.0
network 172.16.10.254 0.0.0.0
# 配置rip 200 绑定VPN2,宣告与总部互联的网络和分支VPN2的网络
rip 200 vpn-instance vpn2
undo summary
version 2
network 20.1.1.1 0.0.0.0
network 172.16.20.254 0.0.0.0
# 不重要的dhcp
dhcp enable
#
vlan 10
#
vlan 20
# 不重要的dhcp
dhcp server ip-pool vlan10
vpn-instance vpn1
gateway-list 172.16.10.254
network 172.16.10.0 mask 255.255.255.0
# 不重要的dhcp
dhcp server ip-pool vlan20
vpn-instance vpn2
gateway-list 172.16.20.254
network 172.16.20.0 mask 255.255.255.0
# Vlan-interface10为VPN1网络网关
interface Vlan-interface10
ip binding vpn-instance vpn1
ip address 172.16.10.254 255.255.255.0
# Vlan-interface20为VPN1网络网关
interface Vlan-interface20
ip binding vpn-instance vpn2
ip address 172.16.20.254 255.255.255.0
# 与总部互联物理接口
interface GigabitEthernet1/0/3
port link-mode route
# 使用子接口与总部互联,绑定VPN1
interface GigabitEthernet1/0/3.10
ip binding vpn-instance vpn1
ip address 10.1.1.1 255.255.255.252
# 使用子接口与总部互联,绑定VPN2
interface GigabitEthernet1/0/3.20
ip binding vpn-instance vpn2
ip address 20.1.1.1 255.255.255.252
# 不重要
interface GigabitEthernet1/0/1
port access vlan 10
stp edged-port
# 不重要
interface GigabitEthernet1/0/2
port access vlan 20
stp edged-port
#
HQ_ROUTER
#
sysname HQ_ROUTER
#
ip vpn-instance vpn1
#
ip vpn-instance vpn2
# 配置rip 100 绑定VPN1,宣告与分支互联的网络,与HQ_SW互联的网络,引入手动配置的去往PC_8主机的路由
rip 100 vpn-instance vpn1
undo summary
version 2
network 10.1.1.2 0.0.0.0
network 100.1.1.1 0.0.0.0
import-route static
# 配置rip 200 绑定VPN2,宣告与分支互联的网络,与HQ_SW互联的网络
rip 200 vpn-instance vpn2
undo summary
version 2
network 20.1.1.2 0.0.0.0
network 100.1.1.1 0.0.0.0
#
vlan 111
#
vlan 222
# 与HQ_SW VPN1 互联vlanif接口
interface Vlan-interface111
ip binding vpn-instance vpn1
ip address 100.1.1.1 255.255.255.252
# 与HQ_SW VPN2 互联vlanif接口
interface Vlan-interface222
ip binding vpn-instance vpn2
ip address 100.1.1.1 255.255.255.252
# 与分支互联物理接口
interface GigabitEthernet0/0
port link-mode route
combo enable copper
# 使用子接口与分支互联,绑定VPN1
interface GigabitEthernet0/0.10
ip binding vpn-instance vpn1
ip address 10.1.1.2 255.255.255.252
vlan-type dot1q vid 10
# 使用子接口与分支互联,绑定VPN2
interface GigabitEthernet0/0.20
ip binding vpn-instance vpn2
ip address 20.1.1.2 255.255.255.252
vlan-type dot1q vid 20
# 与HQ_SW互联的物理接口
interface GigabitEthernet0/1
port link-mode bridge
port link-type trunk
port trunk permit vlan all
combo enable copper
# 在vpn1网络中配置的去往PC_8主机的路由
ip route-static vpn-instance vpn1 192.168.40.200 32 vpn-instance vpn2 100.1.1.2
#
HQ_SW
#
sysname HQ_SW
#
ip vpn-instance vpn1
#
ip vpn-instance vpn2
# 配置rip 100 绑定VPN1,宣告与HQ_ROUTER互联的网络和总部VPN1的网络,注意有一条路由过滤,因为在HQ_ROUTER中引入了手动配置的静态的路由,而在HQ_SW VPN1网络中不需要
rip 100 vpn-instance vpn1
undo summary
version 2
network 100.1.1.2 0.0.0.0
network 192.168.30.254 0.0.0.0
filter-policy prefix-list filter_192.168.40.200 import
# 配置rip 200 绑定VPN2,宣告与HQ_ROUTER互联的网络和总部VPN2的网络
rip 200 vpn-instance vpn2
undo summary
version 2
network 100.1.1.2 0.0.0.0
network 192.168.40.254 0.0.0.0
# 不重要的dhcp
dhcp enable
#
vlan 30
#
vlan 40
#
vlan 111
#
vlan 222
# 不重要的dhcp
dhcp server ip-pool vlan30
vpn-instance vpn1
gateway-list 192.168.30.254
network 192.168.30.0 mask 255.255.255.0
# 不重要的dhcp
dhcp server ip-pool vlan40
vpn-instance vpn2
gateway-list 192.168.40.254
network 192.168.40.0 mask 255.255.255.0
forbidden-ip 192.168.40.200
# vlan30为VPN1网络网关
interface Vlan-interface30
ip binding vpn-instance vpn1
ip address 192.168.30.254 255.255.255.0
# vlan40为VPN1网络网关
interface Vlan-interface40
ip binding vpn-instance vpn2
ip address 192.168.40.254 255.255.255.0
packet-filter 3001 inbound
# 与HQ_ROUTER VPN1 互联vlanif接口
interface Vlan-interface111
ip binding vpn-instance vpn1
ip address 100.1.1.2 255.255.255.252
# 与HQ_ROUTER VPN2 互联vlanif接口
interface Vlan-interface222
ip binding vpn-instance vpn2
ip address 100.1.1.2 255.255.255.252
# 与HQ_ROUTER互联的物理接口
interface GigabitEthernet1/0/1
port link-mode bridge
port link-type trunk
port trunk permit vlan all
combo enable fiber
# 配置前缀列表,过滤从HQ_ROUTER学习到的特殊主机路由
ip prefix-list filter_192.168.40.200 index 10 deny 192.168.40.2 32
ip prefix-list filter_192.168.40.200 index 20 permit 0.0.0.0 0 less-equal 32
# 配置总部VPN2网络到分支VPN1网络的路由
ip route-static vpn-instance vpn2 172.16.10.0 24 vpn-instance vpn1 100.1.1.1
# 限制除PC_8外去往分支VPN1网络的流量
acl advanced 3001
rule 0 permit ip source 192.168.40.200 0 destination 172.16.10.0 0.0.0.255
rule 5 deny ip source 192.168.40.0 0.0.0.255 destination 172.16.10.0 0.0.0.255
rule 10 permit ip
#