在公众号【易联无界】看到文章 [华为2021-2022全球总决赛实验题 ]
研究研究,搓一搓
文章很长,建议电脑端网页查看
文章末尾,附上ensp拓扑文件和配置导出文件
说明
- ensp版本:1.3.00.100 V100R003C00SPC100
- 电脑:Win10 ltsc (CPU:不配拥有名称,RAM=16GB)
- FW桥接网卡只是直观查看会话和状态
- 我电脑跑这图是真的卡
- 遇到FW启动错误代码40,建议先启动两台FW,再启动其他设备
- AR路由器我整不出G0/0/3接口,使用G3/0/0代替
- Video server 地址修改为100.1.100.2
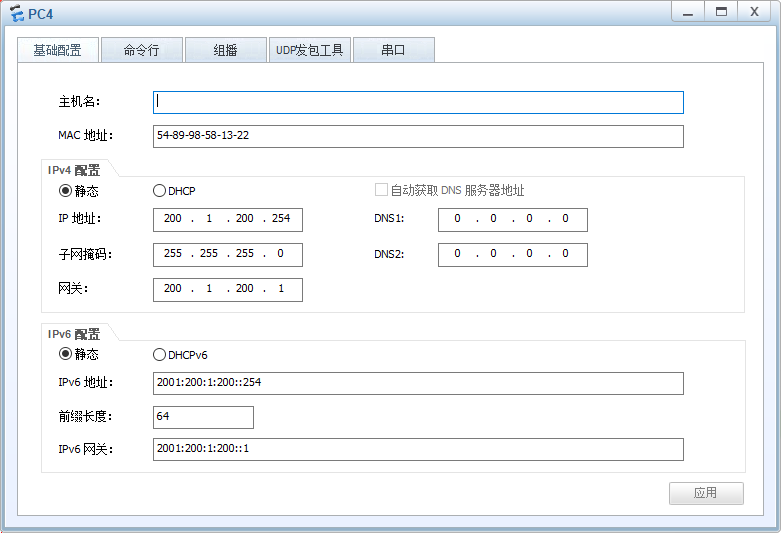
- PC4手动配置IPv6地址 2001:200:1:200::254/64
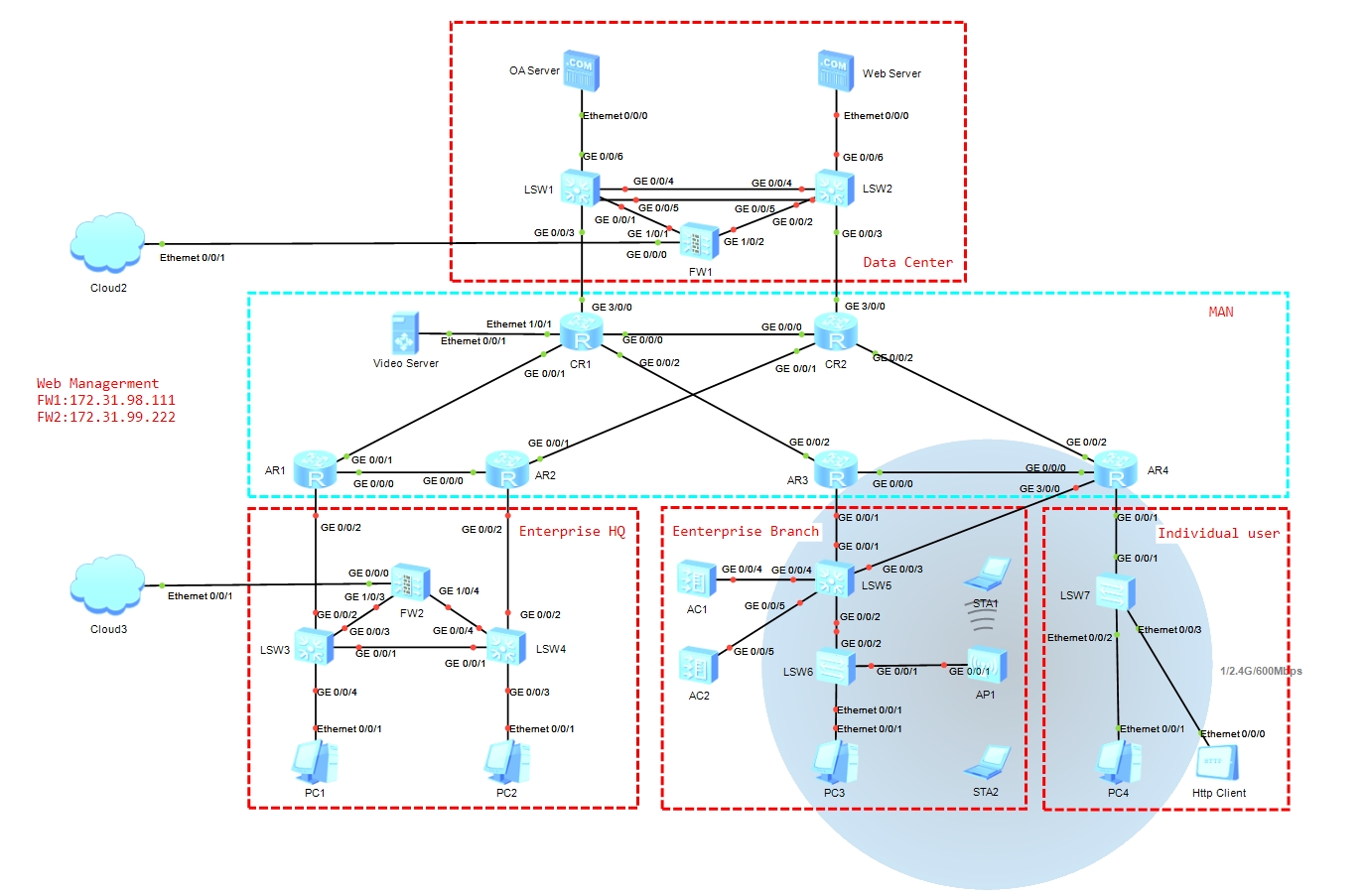
实验拓扑
需求分析和配置
4.1 Task 1: Basic Data Configuration
4.1.1 Configuring VLANs
- 按照给出的表格数据配置对应设备的vlan、Trunk、Access
- 路由器接口注意配置子接口dot1q termination vid xx ,arp broadcast enable
- 防火墙接口注意配置 vlan-type dot1q xx
4.1.2 Configuring IP Addresses
- 按照给出的表格数据配置对应设备的IP地址、IPv6地址
- 对于vrf接口和防火墙vsys接口,可先配置description描述
- 配置必要的接口描述(后续配置静态路由时快速查看和检查)
4.2 Task 2: Route Deployment on the MAN
4.2.1 Configuring IGP
- 配置IS-IS,进程号100,区域ID 86.0010,level-2路由器,系统ID的换算,直连不选举DIS
- 配置接口cost,(设置cost-style wide)
- IS-IS收敛参数,spf计算参数,lsp 快速泛洪
- IS-IS hello md5认证
- IPv6 IS-IS,IPv6的IS-IS cost
AR1/AR2/AR3/AR4/CR1/CR2
# 区域ID + 系统ID换算 AR1: network-entity 86.0010.0010.0100.1001.00 AR2: network-entity 86.0010.0010.0100.1002.00 AR3: network-entity 86.0010.0010.0100.1003.00 AR4: network-entity 86.0010.0010.0100.1004.00 CR1: network-entity 86.0010.0010.0100.1005.00 CR2: network-entity 86.0010.0010.0100.1006.00 # # AR1 bfd # isis 100 # level-2路由器 is-level level-2 # 设置IS-IS设备接收和发送路由的开销类型,默认narro的值范围为1-63,wide的值范围1-16777215 cost-style wide # IS-IS收敛参数 timer lsp-generation 1 50 100 level-2 # lsp 快速泛洪 flash-flood level-2 # bfd bfd all-interfaces enable network-entity 86.0010.0010.0100.1001.00 # spf计算参数 timer spf 1 20 100 # IPv6拓扑类型 ipv6 enable topology ipv6 # # loopback 0 接口运行isis interface LoopBack0 isis enable 100 isis ipv6 enable 100 #AR1
# interface GigabitEthernet0/0/0 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 200 level-2 isis cost 200 level-2 # interface GigabitEthernet0/0/1 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 100 level-2 isis cost 100 level-2 #AR2
# interface GigabitEthernet0/0/0 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 200 level-2 isis cost 200 level-2 # interface GigabitEthernet0/0/1 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 100 level-2 isis cost 100 level-2 #AR3
# interface GigabitEthernet0/0/0 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 200 level-2 isis cost 200 level-2 # interface GigabitEthernet0/0/2 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 100 level-2 isis cost 100 level-2 #AR4
# interface GigabitEthernet0/0/0 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 200 level-2 isis cost 200 level-2 # interface GigabitEthernet0/0/2 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 100 level-2 isis cost 100 level-2 #CR1
# interface GigabitEthernet0/0/0 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 300 level-2 isis cost 300 level-2 # interface GigabitEthernet0/0/1 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 100 level-2 isis cost 100 level-2 # interface GigabitEthernet0/0/2 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 100 level-2 isis cost 100 level-2 #CR2
# interface GigabitEthernet0/0/0 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 300 level-2 isis cost 300 level-2 # interface GigabitEthernet0/0/1 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 100 level-2 isis cost 100 level-2 # interface GigabitEthernet0/0/2 isis enable 100 isis ipv6 enable 100 isis circuit-type p2p isis authentication-mode md5 Huawei@123 isis ipv6 cost 100 level-2 isis cost 100 level-2 #验证
dis ip routing-table protocol isis (配置完成6台路由器,查看路由表学到其他5台路由器的loopback0地址)
<AR1>dis ip routing-table protocol isis | i 1.1.1. Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Public routing table : ISIS Destinations : 10 Routes : 11 ISIS routing table status : <Active> Destinations : 10 Routes : 11 Destination/Mask Proto Pre Cost Flags NextHop Interface 1.1.1.2/32 ISIS-L2 15 200 D 10.1.2.2 GigabitEthernet0/0/0 1.1.1.3/32 ISIS-L2 15 200 D 10.1.5.1 GigabitEthernet0/0/1 1.1.1.4/32 ISIS-L2 15 400 D 10.1.5.1 GigabitEthernet0/0/1 1.1.1.5/32 ISIS-L2 15 100 D 10.1.5.1 GigabitEthernet0/0/1 1.1.1.6/32 ISIS-L2 15 300 D 10.1.2.2 GigabitEthernet0/0/0 ISIS routing table status : <Inactive> Destinations : 0 Routes : 0 <AR1>dis ipv routing-table protocol isis (IPv6)
<CR2>dis ipv routing-table protocol isis | i 2022:: Public Routing Table : ISIS Summary Count : 11 ISIS Routing Table's Status : < Active > Summary Count : 11 Destination : 2022::1 PrefixLength : 128 Destination : 2022::2 PrefixLength : 128 Destination : 2022::3 PrefixLength : 128 Destination : 2022::4 PrefixLength : 128 Destination : 2022::5 PrefixLength : 128 ISIS Routing Table's Status : < Inactive > Summary Count : 0 <CR2>
4.2.2 Configuring BGP
- 配置MAN IBGP,AS64812,CR1和CR2为RR反射器(v4,vpnv4,v6),使用对等体组命令,使用loopback0作为源
- 配置与DataCenter的EBGP,AS62022,使用loopback0(EBGP多跳)(v4,v6),LSW1和LSW2配置指向CR1,CR2的默认路由(后边有配置静态路由的需求)
- 配置CR1,CR2 的v4 EBGP邻居md5认证
- 配置CR1,CR2路由阻尼dampening
- 配置CR1和CR2条件通告默认路由到AR1-AR4
- 配置AR1,和AR3优选下一跳CR1,AR2和AR4优选下一跳CR2
- 配置BGP network组播源服务器网段
CR1
# bgp 64812 router-id 1.1.1.5 group ibgpv4 internal peer ibgpv4 connect-interface LoopBack0 group ibgpv6 internal peer ibgpv6 connect-interface LoopBack0 peer 1.1.1.1 group ibgpv4 peer 1.1.1.2 group ibgpv4 peer 1.1.1.3 group ibgpv4 peer 1.1.1.4 group ibgpv4 peer 1.1.1.6 group ibgpv4 peer 2022::1 group ibgpv6 peer 2022::2 group ibgpv6 peer 2022::3 group ibgpv6 peer 2022::4 group ibgpv6 peer 2022::6 group ibgpv6 peer 1.1.1.8 as-number 62022 peer 1.1.1.8 ebgp-max-hop 2 peer 1.1.1.8 connect-interface LoopBack0 peer 1.1.1.8 password cipher Huawei@123 peer 2022::8 as-number 62022 peer 2022::8 ebgp-max-hop 2 peer 2022::8 connect-interface LoopBack0 # ipv4-family unicast reflector cluster-id 56.56.56.56 dampening 10 2000 3000 10000 network 100.1.100.0 255.255.255.252 peer ibgpv4 reflect-client peer ibgpv4 next-hop-local peer ibgpv4 default-route-advertise conditional-route-match-all 100.1.200.0 255.255.255.0 undo peer 1.1.1.6 default-route-advertise peer 1.1.1.8 enable # ipv6-family unicast reflector cluster-id 56.56.56.56 dampening 10 2000 3000 10000 peer 2022::8 enable peer ibgpv6 enable peer ibgpv6 reflect-client peer ibgpv6 next-hop-local peer 2022::1 group ibgpv6 peer 2022::2 group ibgpv6 peer 2022::3 group ibgpv6 peer 2022::4 group ibgpv6 peer 2022::6 group ibgpv6 # ipv4-family vpnv4 reflector cluster-id 56.56.56.56 undo policy vpn-target peer ibgpv4 enable peer ibgpv4 reflect-client peer 1.1.1.1 group ibgpv4 peer 1.1.1.2 group ibgpv4 peer 1.1.1.3 group ibgpv4 peer 1.1.1.4 group ibgpv4 # # ip route-static 1.1.1.8 255.255.255.255 10.5.8.1 # ipv6 route-static 2022::8 128 2001:5:8::1 #CR2
# bgp 64812 router-id 1.1.1.6 group ibgpv4 internal peer ibgpv4 connect-interface LoopBack0 group ibgpv6 internal peer ibgpv6 connect-interface LoopBack0 peer 1.1.1.1 group ibgpv4 peer 1.1.1.2 group ibgpv4 peer 1.1.1.3 group ibgpv4 peer 1.1.1.4 group ibgpv4 peer 1.1.1.5 group ibgpv4 peer 2022::1 group ibgpv6 peer 2022::2 group ibgpv6 peer 2022::3 group ibgpv6 peer 2022::4 group ibgpv6 peer 2022::5 group ibgpv6 peer 1.1.1.9 as-number 62022 peer 1.1.1.9 ebgp-max-hop 2 peer 1.1.1.9 connect-interface LoopBack0 peer 1.1.1.9 password cipher Huawei@123 peer 2022::9 as-number 62022 peer 2022::9 ebgp-max-hop 2 peer 2022::9 connect-interface LoopBack0 # ipv4-family unicast reflector cluster-id 56.56.56.56 dampening 10 2000 3000 10000 network 100.1.100.0 255.255.255.252 peer ibgpv4 reflect-client peer ibgpv4 next-hop-local peer ibgpv4 default-route-advertise conditional-route-match-all 100.1.200.0 255.255.255.0 undo peer 1.1.1.5 default-route-advertise peer 1.1.1.9 enable # ipv6-family unicast reflector cluster-id 56.56.56.56 dampening 10 2000 3000 10000 peer 2022::9 enable peer ibgpv6 enable peer ibgpv6 reflect-client peer ibgpv6 next-hop-local peer 2022::1 group ibgpv6 peer 2022::2 group ibgpv6 peer 2022::3 group ibgpv6 peer 2022::4 group ibgpv6 peer 2022::5 group ibgpv6 # ipv4-family vpnv4 reflector cluster-id 56.56.56.56 undo policy vpn-target peer ibgpv4 enable peer ibgpv4 reflect-client peer 1.1.1.1 group ibgpv4 peer 1.1.1.2 group ibgpv4 peer 1.1.1.3 group ibgpv4 peer 1.1.1.4 group ibgpv4 # # ip route-static 1.1.1.9 255.255.255.255 10.6.9.1 # ipv6 route-static 2022::9 128 2001:6:9::1 #AR1/AR2/AR3/AR4/,注意修改各路由器的router-id
# AR1 bgp 64812 router-id 1.1.1.1 peer 1.1.1.5 as-number 64812 peer 1.1.1.5 connect-interface LoopBack0 peer 1.1.1.6 as-number 64812 peer 1.1.1.6 connect-interface LoopBack0 peer 2022::5 as-number 64812 peer 2022::5 connect-interface LoopBack0 peer 2022::6 as-number 64812 peer 2022::6 connect-interface LoopBack0 # ipv4-family unicast peer 1.1.1.5 next-hop-local peer 1.1.1.6 next-hop-local # ipv6-family unicast peer 2022::5 enable peer 2022::5 next-hop-local peer 2022::6 enable peer 2022::6 next-hop-local # ipv4-family vpnv4 policy vpn-target peer 1.1.1.5 enable peer 1.1.1.6 enable #AR1/AR3
# bgp 64812 # ipv4-family unicast peer 1.1.1.5 preferred-value 2000 peer 1.1.1.6 preferred-value 1000 #AR2/AR4
# bgp 64812 # ipv4-family unicast peer 1.1.1.5 preferred-value 1000 peer 1.1.1.6 preferred-value 2000 #LSW1
# ip route-static 0.0.0.0 0.0.0.0 10.5.8.2 # ipv6 route-static :: 0 2001:5:8::2 # bgp 62022 router-id 1.1.1.8 peer 1.1.1.5 as-number 64812 peer 1.1.1.5 ebgp-max-hop 2 peer 1.1.1.5 connect-interface LoopBack0 peer 1.1.1.5 password cipher Huawei@123 peer 2022::5 as-number 64812 peer 2022::5 ebgp-max-hop 2 peer 2022::5 connect-interface LoopBack0 # ipv4-family unicast peer 1.1.1.5 enable # ipv6-family unicast peer 2022::5 enable #LSW2
# ip route-static 0.0.0.0 0.0.0.0 10.6.9.2 # ipv6 route-static :: 0 2001:6:9::2 # bgp 62022 router-id 1.1.1.9 peer 1.1.1.6 as-number 64812 peer 1.1.1.6 ebgp-max-hop 2 peer 1.1.1.6 connect-interface LoopBack0 peer 1.1.1.6 password cipher Huawei@123 peer 2022::6 as-number 64812 peer 2022::6 ebgp-max-hop 2 peer 2022::6 connect-interface LoopBack0 # ipv4-family unicast peer 1.1.1.6 enable # ipv6-family unicast peer 2022::6 enable #验证
dis bgp peer (IPv4peer)
<AR1>dis bgp peer BGP local router ID : 1.1.1.1 Local AS number : 64812 Total number of peers : 2 Peers in established state : 2 Peer V AS MsgRcvd MsgSent OutQ Up/Down State PrefRcv 1.1.1.5 4 64812 15 14 0 00:12:14 Established 1 1.1.1.6 4 64812 15 14 0 00:12:14 Established 1 <AR1>dis bgp ipv6 peer (IPv6 peer)
<AR2>dis bgp ipv6 peer BGP local router ID : 1.1.1.2 Local AS number : 64812 Total number of peers : 2 Peers in established state : 2 Peer V AS MsgRcvd MsgSent OutQ Up/Down State PrefRcv 2022::5 4 64812 12 12 0 00:10:23 Established 0 2022::6 4 64812 12 12 0 00:10:22 Established 0 <AR2>dis bgp vpnv4 all peer (vpnv4 peer)
<CR1>dis bgp vpnv4 all peer BGP local router ID : 1.1.1.5 Local AS number : 64812 Total number of peers : 4 Peers in established state : 4 Peer V AS MsgRcvd MsgSent OutQ Up/Down State PrefRcv 1.1.1.1 4 64812 21 23 0 00:19:24 Established 0 1.1.1.2 4 64812 19 21 0 00:17:19 Established 0 1.1.1.3 4 64812 19 21 0 00:17:52 Established 0 1.1.1.4 4 64812 18 20 0 00:16:52 Established 0 <CR1>dis bgp routing-table
<AR4>dis bgp routing-table BGP Local router ID is 1.1.1.4 Status codes: * - valid, > - best, d - damped, h - history, i - internal, s - suppressed, S - Stale Origin : i - IGP, e - EGP, ? - incomplete Total Number of Routes: 2 Network NextHop MED LocPrf PrefVal Path/Ogn *>i 100.1.100.0/30 1.1.1.5 0 100 2000 i * i 1.1.1.5 0 100 1000 i <AR4>dis bgp routing-table 100.1.100.0
<AR4>dis bgp routing-table 100.1.100.0 BGP local router ID : 1.1.1.4 Local AS number : 64812 Paths: 2 available, 1 best, 1 select BGP routing table entry information of 100.1.100.0/30: From: 1.1.1.6 (1.1.1.6) Route Duration: 00h03m40s Relay IP Nexthop: 10.3.4.1 Relay IP Out-Interface: GigabitEthernet0/0/0 Original nexthop: 1.1.1.5 Qos information : 0x0 AS-path Nil, origin igp, MED 0, localpref 100, pref-val 2000, valid, internal, best, select, active, pre 255, IGP cost 300 Originator: 1.1.1.5 Cluster list: 56.56.56.56 Not advertised to any peer yet BGP routing table entry information of 100.1.100.0/30: From: 1.1.1.5 (1.1.1.5) Route Duration: 00h03m40s Relay IP Nexthop: 10.3.4.1 Relay IP Out-Interface: GigabitEthernet0/0/0 Original nexthop: 1.1.1.5 Qos information : 0x0 AS-path Nil, origin igp, MED 0, localpref 100, pref-val 1000, valid, internal, pre 255, IGP cost 300, not preferred for PreVal Not advertised to any peer yet <AR4>
4.3 Task 3: Data Center Internet Service Deployment
4.3.1 Connecting the Web Server to the Network
配置LSW1,LSW2的eth-trunk 12,静态lacp,src-mac 负载均衡
创建vrf intvpn,不传vpnv4用不到RD和RT
vlan200,下配置vrrp,vrid 2,virtual-ip 192.168.200.1/24,LSW2为master,优先级120,抢占延迟20s,track接口G0/0/2状态,失效优先级减21成为backup
配置nqa探测,LSW1-CR1,LSW2-CR2,类型icmp,5s间隔周期探测时间,
配置出向静态路由,backup路由优先级90,看示意图,LSW1-CR1,LSW2-CR2 的默认路由track nqa,配置默认路由备份路由指向 LSW1 LSW2
配置入向静态路由,看示意图
FW1配置安全策略,看示意图
FW1配置NAT映射,策略包含80端口,放行icmp
LSW1和LSW2之间的备份路由在出口全部宕机的情况下的环路处理
BGP network (web服务器公网映射网段路由)
LSW1
# interface GigabitEthernet0/0/4 undo eth-trunk # interface GigabitEthernet0/0/5 undo eth-trunk # interface Eth-Trunk12 mode lacp-static load-balance src-mac # interface GigabitEthernet0/0/4 eth-trunk 12 # interface GigabitEthernet0/0/5 eth-trunk 12 # ip vpn-instance intvpn ipv4-family # interface Vlanif200 description VPN-intvpn ip binding vpn-instance intvpn ip address 192.168.200.8 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.200.1 vrrp vrid 2 preempt-mode timer delay 20 # interface Vlanif30 description VPN-intvpn ip binding vpn-instance intvpn ip address 192.168.3.1 255.255.255.252 # nqa test-instance toCR toCR test-type icmp destination-address ipv4 10.5.8.2 frequency 5 interval seconds 1 timeout 1 probe-count 2 start now # ip route-static 0.0.0.0 0.0.0.0 10.5.8.2 track nqa toCR toCR ip route-static 0.0.0.0 0.0.0.0 192.168.9.2 preference 90 ip route-static 100.1.200.0 255.255.255.0 100.1.4.2 ip route-static vpn-instance intvpn 0.0.0.0 0.0.0.0 192.168.3.2 # # bgp 62022 # ipv4-family unicast network 100.1.200.0 24 # # 阻止LSW1-LSW2备份路由形成的环路 nqa test-instance PREVENT_LOOP PREVENT_LOOP test-type icmp destination-address ipv4 10.6.9.1 frequency 5 interval seconds 1 timeout 1 probe-count 2 start now # ip route-static 10.6.9.1 255.255.255.255 192.168.9.2 ip route-static 0.0.0.0 0.0.0.0 192.168.9.2 preference 90 track nqa PREVENT_LOOP PREVENT_LOOP #LSW2
# interface GigabitEthernet0/0/4 undo eth-trunk # interface GigabitEthernet0/0/5 undo eth-trunk # interface Eth-Trunk12 port link-type trunk port trunk allow-pass vlan 90 100 200 mode lacp-static load-balance src-mac # interface GigabitEthernet0/0/4 eth-trunk 12 # interface GigabitEthernet0/0/5 eth-trunk 12 # ip vpn-instance intvpn ipv4-family # interface Vlanif200 description VPN-intvpn ip binding vpn-instance intvpn ip address 192.168.200.9 255.255.255.0 vrrp vrid 2 virtual-ip 192.168.200.1 vrrp vrid 2 priority 120 vrrp vrid 2 preempt-mode timer delay 20 vrrp vrid 2 track interface GigabitEthernet0/0/2 reduced 21 # interface Vlanif30 description VPN-intvpn ip binding vpn-instance intvpn ip address 192.168.30.1 255.255.255.252 # nqa test-instance toCR toCR test-type icmp destination-address ipv4 10.6.9.2 frequency 5 interval seconds 1 timeout 1 probe-count 2 start now # ip route-static 0.0.0.0 0.0.0.0 10.6.9.2 track nqa toCR toCR ip route-static 0.0.0.0 0.0.0.0 192.168.9.1 preference 90 ip route-static 100.1.200.0 255.255.255.0 100.1.40.2 ip route-static vpn-instance intvpn 0.0.0.0 0.0.0.0 192.168.30.2 # # bgp 62022 # ipv4-family unicast network 100.1.200.0 24 # # 阻止LSW1-LSW2备份路由形成的环路 nqa test-instance PREVENT_LOOP PREVENT_LOOP test-type icmp destination-address ipv4 10.5.8.1 frequency 5 interval seconds 1 timeout 1 probe-count 2 start now # ip route-static 10.5.8.1 255.255.255.255 192.168.9.1 ip route-static 0.0.0.0 0.0.0.0 192.168.9.1 preference 90 track nqa PREVENT_LOOP PREVENT_LOOP #FW1
# ip route-static 0.0.0.0 0.0.0.0 100.1.40.1 ip route-static 0.0.0.0 0.0.0.0 100.1.4.1 preference 90 ip route-static 192.168.200.0 255.255.255.0 192.168.30.1 ip route-static 192.168.200.0 255.255.255.0 192.168.3.1 preference 90 # firewall zone untrust add interface GigabitEthernet1/0/1.40 add interface GigabitEthernet1/0/2.40 # firewall zone dmz add interface GigabitEthernet1/0/1.30 add interface GigabitEthernet1/0/2.30 # security-policy rule name untrust2dmz source-zone untrust destination-zone dmz destination-address 192.168.200.0 mask 255.255.255.0 action permit # nat server web_server protocol tcp global 100.1.200.254 www inside 192.168.200.254 www nat server icmp_server protocol icmp global 100.1.200.254 inside 192.168.200.254 #AR4
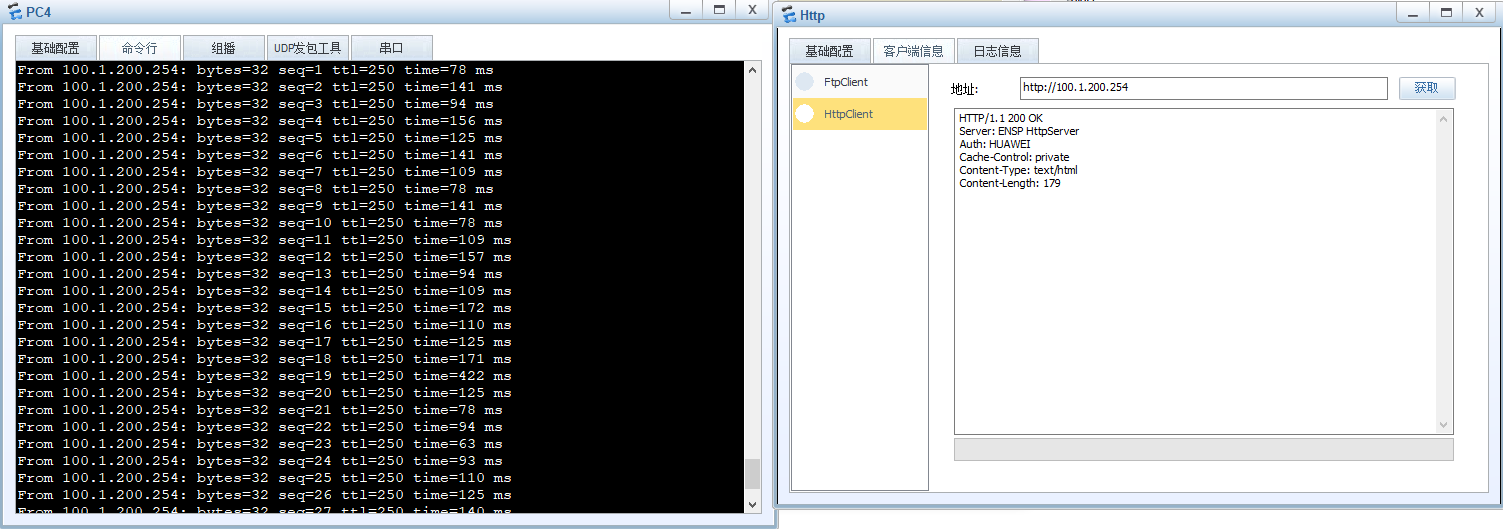
# bgp 64812 # ipv4-family unicast network 200.1.200.0 24 #PC4 ping测试和Http Client 测试
4.3.2 Connecting the Simulated IPv6 Servers to the Network
- LSW1和LSW2创建loopback1,配置IPv6地址
- 配置ospfv3,进程号200,vlanif90 建立邻居,改网络类型不选DR
- BGP 仅 import 两loopback1 IPv6地址,挂上route-map ,prefix配置
- 配置路由聚合,112掩码
LSW1
# ospfv3 200 router-id 1.1.1.8 interface LoopBack1 ipv6 enable ipv6 address 2001:100:1:200::8/128 ospfv3 200 area 0.0.0.0 # interface Vlanif90 ospfv3 200 area 0.0.0.0 ospfv3 network-type p2p # ip ipv6-prefix V6_SERVER permit 2001:100:1:200::8 128 ip ipv6-prefix V6_SERVER permit 2001:100:1:200::9 128 # route-policy V6_SERVER permit node 10 if-match ipv6 address prefix-list V6_SERVER # bgp 62022 ipv6-family unicast aggregate 2001:100:1:200:: 112 detail-suppressed import-route ospfv3 200 route-policy V6_SERVERLSW2
# ospfv3 200 router-id 1.1.1.9 # interface LoopBack1 ipv6 enable ipv6 address 2001:100:1:200::9/128 ospfv3 200 area 0.0.0.0 # interface Vlanif90 ospfv3 200 area 0.0.0.0 ospfv3 network-type p2p # ip ipv6-prefix V6_SERVER permit 2001:100:1:200::8 128 ip ipv6-prefix V6_SERVER permit 2001:100:1:200::9 128 # route-policy V6_SERVER permit node 10 if-match ipv6 address prefix-list V6_SERVER # bgp 62022 ipv6-family unicast aggregate 2001:100:1:200:: 112 detail-suppressed import-route ospfv3 200 route-policy V6_SERVERAR4
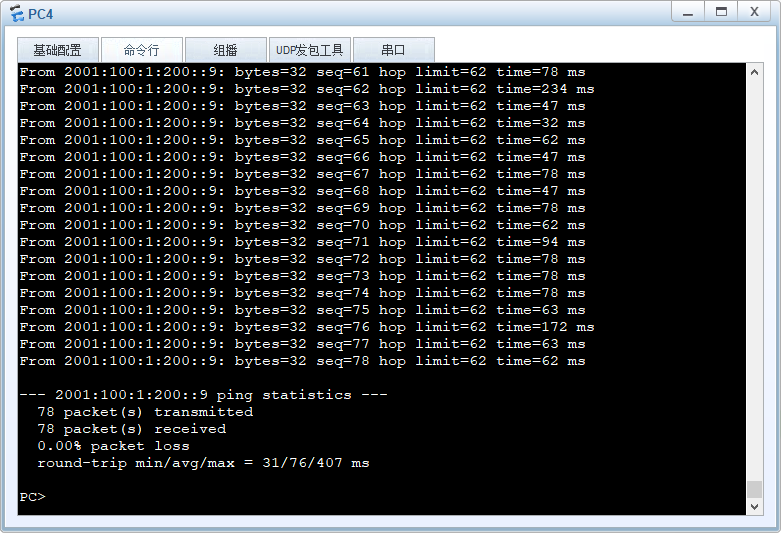
bgp 64812 ipv6-family unicast network 2001:200:1:200:: 64PC4 配置IPv6地址-2001:200:1:200::254/64; IPv6网关-2001:200:1:200::1
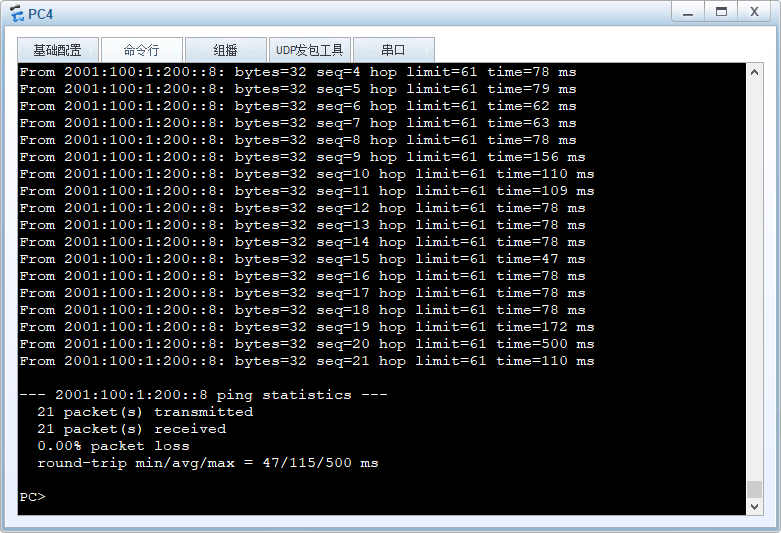
PC4 ping测试
4.3.3 Configuring Security Protection on the Firewall
- 拉黑200.1.200.200地址
FW1
[FW1]firewall blacklist enable [FW1]firewall blacklist item source-ip 200.1.200.200
4.4 Task 4: Enterprise HQ Network Deployment
4.4.1 Configuring a Layer 2 Network
- 端口安全,动态安全地址,mac 抖动,最大mac地址2,aging time 1200m
- 端口学习mac地址的优先级
LSW3
# interface GigabitEthernet0/0/2 mac-learning priority 3 # interface GigabitEthernet0/0/4 port-security enable port-security protect-action shutdown port-security max-mac-num 2 port-security mac-address sticky port-security aging-time 1200 #LSW4
# interface GigabitEthernet0/0/2 mac-learning priority 3 # interface GigabitEthernet0/0/3 port-security enable port-security protect-action shutdown port-security max-mac-num 2 port-security mac-address sticky port-security aging-time 1200 #
4.4.2 Configuring Basic Services on the Firewall
- 配置安全策略,HQ 172.16.100.0/24和Branch172.17.100.0/24上互联网(NAT need)
- 配置安全策略,HQ 172.16.101.0/24 访问OA 192.168.100.0/24(FW1上做了映射公网)
- 配置ip-link ,FW2-AR1, FW2-AR2,搭配后续的出向默认路由使用
- 出向静态路由
- 入向静态路由,AR1和AR2 (200.1.100.0/24)指向 FW2;FW2配置特定主备路由指向LSW3 LSW4
- 配置NAT,接入互联网,最终ping通WEB服务器和Video服务器需要这个,转换地址池200.1.100.2 - 200.1.100.10
FW2
# firewall zone trust add interface GigabitEthernet1/0/3.30 add interface GigabitEthernet1/0/4.40 # firewall zone untrust add interface GigabitEthernet1/0/3.60 add interface GigabitEthernet1/0/4.70 # ip-link check enable ip-link name toar1 destination 200.1.6.1 interface GigabitEthernet1/0/3.60 mode arp ip-link name toar2 destination 200.1.7.1 interface GigabitEthernet1/0/4.70 mode arp # security-policy rule name trust2untrust01 source-zone trust destination-zone untrust source-address 172.16.100.0 mask 255.255.255.0 source-address 172.17.100.0 mask 255.255.255.0 action permit rule name trust2untrust02 source-zone trust destination-zone untrust source-address 172.16.101.0 mask 255.255.255.0 destination-address 192.168.100.0 mask 255.255.255.0 action permit # ip route-static 0.0.0.0 0.0.0.0 200.1.6.1 track ip-link toar1 ip route-static 0.0.0.0 0.0.0.0 200.1.7.1 track ip-link toar2 ip route-static 172.16.100.0 255.255.255.0 172.16.3.1 ip route-static 172.16.100.0 255.255.255.0 172.16.4.1 preference 90 ip route-static 172.16.101.0 255.255.255.0 172.16.4.1 ip route-static 172.16.101.0 255.255.255.0 172.16.3.1 preference 90 ip route-static 172.17.100.0 255.255.255.0 172.16.3.1 ip route-static 172.17.100.0 255.255.255.0 172.16.4.1 # nat address-group addressgroup1 0 mode pat section 0 200.1.100.2 200.1.100.10 # nat-policy rule name policy_nat1 source-zone trust destination-zone untrust source-address 172.16.100.0 mask 255.255.255.0 source-address 172.17.100.0 mask 255.255.255.0 destination-address 100.1.0.0 mask 255.255.0.0 action source-nat address-group addressgroup1 #LSW3
# ip route-static 0.0.0.0 0.0.0.0 172.16.3.2 #LSW4
# ip route-static 0.0.0.0 0.0.0.0 172.16.4.2 #AR1
# ip route-static 200.1.100.0 255.255.255.0 200.1.6.2 # bgp 64812 # ipv4-family unicast import-route static #AR2
# ip route-static 200.1.100.0 255.255.255.0 200.1.7.2 # bgp 64812 # ipv4-family unicast import-route static #验证
4.4.3 Configuring URL Filtering on the Firewall
url-filter profile的配置,去网页点点看
# profile type url-filter name url_profile_deny add blacklist url www.example1.com add blacklist url www.example2.com category pre-defined control-level medium https-filter enable #
4.4.4 Configuring the IPS Function on the Firewall
ips profile的配置,去网页点点看
# profile type ips name Profile_ips_pc collect-attack-evidence enable # 依赖硬盘,ensp不起作用 signature-set name filter_web target client severity high protocol HTTP # security-policy rule name trust2untrust01 profile ips Profile_ips_pc #
4.4.5 Configuring Traffic Management on the Firewall
配置流量管理,去网页点点看
# time-range work_time period-range 09:00:00 to 18:00:00 working-day # traffic-policy profile profile_p2p bandwidth maximum-bandwidth whole both 50000 bandwidth connection-limit whole both 2000 profile profile_email bandwidth guaranteed-bandwidth whole both 100000 bandwidth priority 7 rule name policy_p2p source-zone trust destination-zone untrust source-address address-set 172.16.100.0&172.17.100.0 application app BT application app YouKu action qos profile profile_p2p rule name policy_email source-zone trust destination-zone untrust source-address 172.16.100.0 mask 255.255.255.0 source-address 172.17.100.0 mask 255.255.255.0 application app LotusNotes application app OWA application category Business_Systems sub-category Email action qos profile profile_email #
4.5 Task 5: Enterprise Branch Network Deployment
4.5.1 Configuring DHCP
- LSW5配置DHCP,此DHCP Server后续的无线sta获取地址也需要用到
- DHCP参数,vlanif100接口,dns 8.8.8.8,lease 2d
- LSW6,配置DHCP snooping,上联dhcp server接口trusted
- 可能的bug(PC3和STA1获取不到IP地址,在LSW5去掉DHCP配置再重新刷入配置解决)
LSW5
# dhcp enable # interface Vlanif100 dhcp select interface dhcp server lease day 2 dhcp server dns-list 8.8.8.8 #LSW6
# dhcp enable # dhcp snooping enable arp dhcp-snooping-detect enable # interface Ethernet0/0/1 dhcp snooping check dhcp-rate enable dhcp snooping check dhcp-rate 80 # interface GigabitEthernet0/0/1 port trunk pvid vlan 200 dhcp snooping check dhcp-rate enable dhcp snooping check dhcp-rate 80 # interface GigabitEthernet0/0/2 dhcp snooping enable dhcp snooping trusted #
4.5.2 Configuring a WLAN
- 配置旁挂二层直接转发+ vrrp热备冗余+hsb状态同步
- 黑名单拉黑sta2接入
- 动态拉黑攻击者mac
- 流量模板限速
- ensp要是支持配置同步功能就厉害了
AC1
# dhcp enable # 下面这行说dhcp信息可以从文件恢复,很重要么这点信息? # dhcp server database enable # interface Vlanif200 ip address 172.17.200.2 255.255.255.0 vrrp vrid 1 virtual-ip 172.17.200.1 admin-vrrp vrid 1 vrrp vrid 1 priority 200 dhcp select interface dhcp server excluded-ip-address 172.17.200.1 172.17.200.3 # capwap source ip-address 172.17.200.1 # wlan # 流量模板 traffic-profile name wlan-traffic rate-limit client up 5000 rate-limit vap up 100000 rate-limit client down 10000 rate-limit vap down 500000 # 安全模板 security-profile name wlan-security security wpa-wpa2 psk pass-phrase Huawei@123 aes # 黑名单拉黑sta2 sta-blacklist-profile name sta-blacklist sta-mac 5489-988a-0449 # 空白的白名单 sta-whitelist-profile name sta-whitelist # SSID模板 ssid-profile name wlan-ssid ssid ICT2022 # VAP模板 vap-profile name wlan-vap service-vlan vlan-id 100 sta-access-mode whitelist sta-whitelist ssid-profile wlan-ssid security-profile wlan-security traffic-profile wlan-traffic # WIDS模板 wids-profile name wlan-wids brute-force-detect interval 80 brute-force-detect threshold 5 brute-force-detect quiet-time 800 dynamic-blacklist enable # AP系统模板 ap-system-profile name wlan-system dynamic-blacklist aging-time 300 sta-access-mode blacklist sta-blacklist # AP组 ap-group name ap-group ap-system-profile wlan-system wids-profile wlan-wids radio 0 vap-profile wlan-vap wlan 1 ap-id 0 type-id 61 ap-mac 00e0-fcf8-2fb0 ap-sn 2102354483106349735D ap-name AP1 ap-group ap-group # hsb-service 0 service-ip-port local-ip 172.17.200.2 peer-ip 172.17.200.3 local-data-port 10241 peer-data-port 10241 # hsb-group 0 track vrrp vrid 1 interface Vlanif200 bind-service 0 hsb enable # 配置完成其他配置再启用查看状态 # hsb-service-type access-user hsb-group 0 # hsb-service-type dhcp hsb-group 0 # hsb-service-type ap hsb-group 0 #AC2 ,修改参数即可,wlan配置与AC 1 一致,粘贴注意有时需要输入 Y 确认
# dhcp enable # interface Vlanif200 ip address 172.17.200.3 255.255.255.0 vrrp vrid 1 virtual-ip 172.17.200.1 admin-vrrp vrid 1 dhcp select interface dhcp server excluded-ip-address 172.17.200.1 172.17.200.3 # capwap source ip-address 172.17.200.1 # wlan # 流量模板 traffic-profile name wlan-traffic rate-limit client up 5000 rate-limit vap up 100000 rate-limit client down 10000 rate-limit vap down 500000 # 安全模板 security-profile name wlan-security security wpa-wpa2 psk pass-phrase Huawei@123 aes # 黑名单拉黑sta2 sta-blacklist-profile name sta-blacklist sta-mac 5489-988a-0449 # 空白的白名单 sta-whitelist-profile name sta-whitelist # SSID模板 ssid-profile name wlan-ssid ssid ICT2022 # VAP模板 vap-profile name wlan-vap service-vlan vlan-id 100 sta-access-mode whitelist sta-whitelist ssid-profile wlan-ssid security-profile wlan-security traffic-profile wlan-traffic # WIDS模板 wids-profile name wlan-wids brute-force-detect interval 80 brute-force-detect threshold 5 brute-force-detect quiet-time 800 dynamic-blacklist enable # AP系统模板 ap-system-profile name wlan-system dynamic-blacklist aging-time 300 sta-access-mode blacklist sta-blacklist # AP组 ap-group name ap-group ap-system-profile wlan-system wids-profile wlan-wids radio 0 vap-profile wlan-vap wlan 1 ap-id 0 type-id 61 ap-mac 00e0-fcf8-2fb0 ap-sn 2102354483106349735D ap-name AP1 ap-group ap-group # hsb-service 0 service-ip-port local-ip 172.17.200.3 peer-ip 172.17.200.2 local-data-port 10241 peer-data-port 10241 # hsb-group 0 track vrrp vrid 1 interface Vlanif200 bind-service 0 hsb enable # hsb-service-type access-user hsb-group 0 # hsb-service-type dhcp hsb-group 0 # hsb-service-type ap hsb-group 0 #校验
dis vrrp
[AC1]dis vrrp Vlanif200 | Virtual Router 1 State : Master Virtual IP : 172.17.200.1 Master IP : 172.17.200.2 PriorityRun : 222 PriorityConfig : 222 MasterPriority : 222 Preempt : YES Delay Time : 0 s TimerRun : 1 s TimerConfig : 1 s Auth type : NONE Virtual MAC : 0000-5e00-0101 Check TTL : YES Config type : admin-vrrp Backup-forward : disabled Create time : 2024-07-16 21:14:14 UTC-05:13 Last change time : 2024-07-16 21:14:27 UTC-05:13 [AC1] [AC2]dis vrrp Vlanif200 | Virtual Router 1 State : Backup Virtual IP : 172.17.200.1 Master IP : 172.17.200.2 PriorityRun : 111 PriorityConfig : 111 MasterPriority : 222 Preempt : YES Delay Time : 0 s TimerRun : 1 s TimerConfig : 1 s Auth type : NONE Virtual MAC : 0000-5e00-0101 Check TTL : YES Config type : admin-vrrp Backup-forward : disabled Create time : 2024-07-16 20:19:15 UTC-05:13 Last change time : 2024-07-16 21:14:58 UTC-05:13dis hsb-group 0
[AC1]dis hsb-group 0 Hot Standby Group Information: ---------------------------------------------------------- HSB-group ID : 0 Vrrp Group ID : 1 Vrrp Interface : Vlanif200 Service Index : 0 Group Vrrp Status : Master Group Status : Active Group Backup Process : Realtime Peer Group Device Name : AC6005 Peer Group Software Version : V200R007C10SPC300B220 Group Backup Modules : Access-user DHCP AP ---------------------------------------------------------- [AC1] [AC2]dis hsb-group 0 Hot Standby Group Information: ---------------------------------------------------------- HSB-group ID : 0 Vrrp Group ID : 1 Vrrp Interface : Vlanif200 Service Index : 0 Group Vrrp Status : Backup Group Status : Inactive Group Backup Process : Realtime Peer Group Device Name : AC6005 Peer Group Software Version : V200R007C10SPC300B220 Group Backup Modules : Access-user DHCP AP ---------------------------------------------------------- [AC2]dis hsb-service 0
[AC1]dis hsb-service 0 Hot Standby Service Information: ---------------------------------------------------------- Local IP Address : 172.17.200.2 Peer IP Address : 172.17.200.3 Source Port : 10241 Destination Port : 10241 Keep Alive Times : 5 Keep Alive Interval : 3 Service State : Connected Service Batch Modules : ---------------------------------------------------------- [AC1] [AC2]dis hsb-service 0 Hot Standby Service Information: ---------------------------------------------------------- Local IP Address : 172.17.200.3 Peer IP Address : 172.17.200.2 Source Port : 10241 Destination Port : 10241 Keep Alive Times : 5 Keep Alive Interval : 3 Service State : Connected Service Batch Modules : ---------------------------------------------------------- [AC2]dis ap all
[AC1]dis ap all Info: This operation may take a few seconds. Please wait for a moment.done. Total AP information: nor : normal [1] --------------------------------------------------------------------------------------------- ID MAC Name Group IP Type State STA Uptime --------------------------------------------------------------------------------------------- 0 00e0-fcf8-2fb0 AP1 ap-group 172.17.200.132 AP4050DN-E nor 1 22M:17S --------------------------------------------------------------------------------------------- Total: 1 [AC1] [AC2]dis ap all Info: This operation may take a few seconds. Please wait for a moment.done. Total AP information: stdby: standby [1] -------------------------------------------------------------------------------------------- ID MAC Name Group IP Type State STA Uptime -------------------------------------------------------------------------------------------- 0 00e0-fcf8-2fb0 AP1 ap-group 172.17.200.132 AP4050DN-E stdby 0 - -------------------------------------------------------------------------------------------- Total: 1 [AC2]dis station all
[AC1]dis station all Rf/WLAN: Radio ID/WLAN ID Rx/Tx: link receive rate/link transmit rate(Mbps) ----------------------------------------------------------------------------------------------------- STA MAC AP ID Ap name Rf/WLAN Band Type Rx/Tx RSSI VLAN IP address SSID ----------------------------------------------------------------------------------------------------- 5489-9811-592c 0 AP1 0/1 2.4G - -/- - 100 172.17.100.254 ICT2022 ----------------------------------------------------------------------------------------------------- Total: 1 2.4G: 1 5G: 0 [AC1] [AC2]dis station all Rf/WLAN: Radio ID/WLAN ID Rx/Tx: link receive rate/link transmit rate(Mbps) -------------------------------------------------------------------------------------------------- STA MAC AP ID Ap name Rf/WLAN Band Type Rx/Tx RSSI VLAN IP address SSID -------------------------------------------------------------------------------------------------- -------------------------------------------------------------------------------------------------- Total: 0 2.4G: 0 5G: 0 [AC2]dis station online-fail-record all
[AC1]dis station online-fail-record all Rf/WLAN: Radio ID/WLAN ID ------------------------------------------------------------------------------ STA MAC AP ID Ap name Rf/WLAN Last record time Reason ------------------------------------------------------------------------------ 5489-988a-0449 0 AP1 0/1 2024-07-19/10:35:02 The STA is in the global blacklist. ------------------------------------------------------------------------------ Total stations: 1 Total records: 1 [AC1]
4.6 Task 6: Service Deployment for Communication Between the Enterprise HQ and Branch
4.6.1 Configuring an MPLSVPN
- 配置ldp,loopback0接口地址为lsr-id,
- AR1/AR2/AR3/AR4,配置vrf entvpn,需要配置RD,RT
- AR1/AR2/LSW3/LSW4配置ospf,进程号100,area0,LSW3/LSW4下发默认路由,面向PC的vlanif接口配置passive被动接口
- LSW5/AR3/AR4/配置EBGP,AS62012,branch使用network起源宣告网段
- vpnv4的反射器,AR1/AR2重分布默认路由进BGP vpn地址族
- 配置AS-PATH添加,route-map,对收到的路由进行选路干预
- LSW5收到的默认路由负载均衡,最大优选路径设置2
- 当HQ两条出口链路中断,LSW3/LSW4的去往branch 172.17.100.0/24的不走FW2的默认路由 ,track默认路由检测互联AR1/AR2的链路
- AR路由器的故障快速切换,在VPN路由收敛前切换
AR1
# mpls lsr-id 1.1.1.1 mpls # mpls ldp # interface GigabitEthernet0/0/0 mpls mpls ldp # interface GigabitEthernet0/0/1 mpls mpls ldp # ip vpn-instance entvpn ipv4-family route-distinguisher 64812:1 vpn frr route-policy VPN-FRR vpn-target 64812:345 both # interface GigabitEthernet0/0/2.10 ip binding vpn-instance entvpn ip address 172.16.1.1 255.255.255.252 # ospf 100 router-id 1.1.1.1 vpn-instance entvpn import-route bgp area 0.0.0.0 network 172.16.1.1 0.0.0.0 # bgp 64812 # ipv4-family vpn-instance entvpn default-route imported import-route ospf 100 # route-policy VPN-FRR permit node 10 apply backup-nexthop auto #AR2
# mpls lsr-id 1.1.1.2 mpls # mpls ldp # interface GigabitEthernet0/0/0 mpls mpls ldp # interface GigabitEthernet0/0/1 mpls mpls ldp # # ip vpn-instance entvpn ipv4-family route-distinguisher 64812:1 vpn frr route-policy VPN-FRR vpn-target 64812:345 both # interface GigabitEthernet0/0/2.20 ip binding vpn-instance entvpn ip address 172.16.2.1 255.255.255.252 # ospf 100 router-id 1.1.1.2 vpn-instance entvpn import-route bgp area 0.0.0.0 network 172.16.2.1 0.0.0.0 # bgp 64812 # ipv4-family vpn-instance entvpn default-route imported import-route ospf 100 # route-policy VPN-FRR permit node 10 apply backup-nexthop auto #AR3
# mpls lsr-id 1.1.1.3 mpls # mpls ldp # interface GigabitEthernet0/0/0 mpls mpls ldp # interface GigabitEthernet0/0/2 pim sm mpls mpls ldp # # ip vpn-instance entvpn ipv4-family route-distinguisher 64812:1 vpn frr route-policy VPN-FRR vpn-target 64812:345 both # interface GigabitEthernet0/0/1.10 ip binding vpn-instance entvpn ip address 172.17.1.1 255.255.255.252 # bgp 64812 # ipv4-family vpn-instance entvpn peer 172.17.1.2 as-number 62012 # route-policy VPN-FRR permit node 10 apply backup-nexthop auto #AR4
# mpls lsr-id 1.1.1.4 mpls # mpls ldp # interface GigabitEthernet0/0/0 mpls mpls ldp # interface GigabitEthernet0/0/2 pim sm mpls mpls ldp # # ip vpn-instance entvpn ipv4-family route-distinguisher 64812:1 vpn frr route-policy VPN-FRR vpn-target 64812:345 both # interface GigabitEthernet3/0/0.20 ip binding vpn-instance entvpn ip address 172.17.2.1 255.255.255.252 # bgp 64812 # ipv4-family vpn-instance entvpn peer 172.17.2.2 as-number 62012 # route-policy VPN-FRR permit node 10 apply backup-nexthop auto #CR1
# mpls lsr-id 1.1.1.5 mpls # mpls ldp # interface GigabitEthernet0/0/0 mpls mpls ldp # interface GigabitEthernet0/0/1 mpls mpls ldp # interface GigabitEthernet0/0/2 mpls mpls ldp #CR2
# mpls lsr-id 1.1.1.6 mpls # mpls ldp # interface GigabitEthernet0/0/0 mpls mpls ldp # interface GigabitEthernet0/0/1 mpls mpls ldp # interface GigabitEthernet0/0/2 mpls mpls ldp #LSW3
# ospf 100 default-route-advertise silent-interface Vlanif100 area 0.0.0.0 network 172.16.1.2 0.0.0.0 network 172.16.5.1 0.0.0.0 network 172.16.100.1 0.0.0.0 # nqa test-instance toAR1 toAR1 test-type icmp destination-address ipv4 172.16.1.1 frequency 5 interval seconds 1 timeout 1 probe-count 2 start now # ip route-static 0.0.0.0 0.0.0.0 172.16.3.2 track nqa toAR1 toAR1LSW4
# ospf 100 default-route-advertise silent-interface Vlanif101 area 0.0.0.0 network 172.16.2.2 0.0.0.0 network 172.16.5.2 0.0.0.0 network 172.16.101.1 0.0.0.0 # nqa test-instance toAR2 toAR2 test-type icmp destination-address ipv4 172.16.2.1 frequency 5 interval seconds 1 timeout 1 probe-count 2 start now # ip route-static 0.0.0.0 0.0.0.0 172.16.4.2 track nqa toAR2 toAR2LSW5
# bgp 62012 peer 172.17.1.1 as-number 64812 peer 172.17.2.1 as-number 64812 # ipv4-family unicast network 172.17.100.0 255.255.255.0 maximum load-balancing 2 peer 172.17.1.1 route-policy AS_PATH_ODD import peer 172.17.2.1 route-policy AS_PATH_EVEN import # # route-policy AS_PATH_EVEN permit node 10 if-match acl 2010 apply as-path 100 additive # route-policy AS_PATH_EVEN permit node 20 # route-policy AS_PATH_ODD permit node 10 if-match acl 2020 apply as-path 100 additive # route-policy AS_PATH_ODD permit node 20 # acl number 2010 rule 5 permit source 172.16.0.0 0.0.254.255 # acl number 2020 rule 5 permit source 172.16.1.0 0.0.254.255 #验证
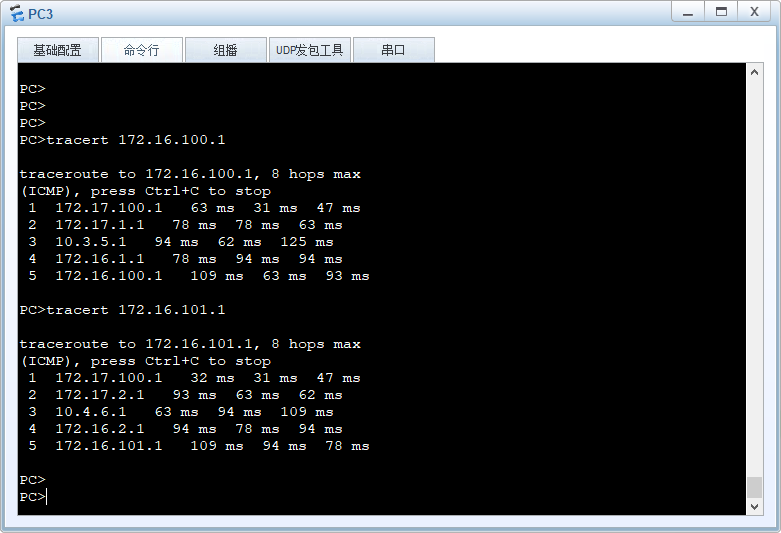
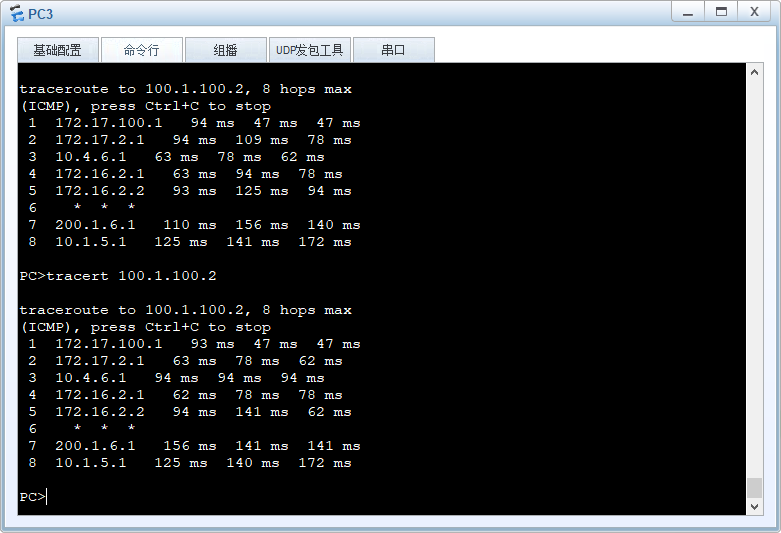
PC3 172.17.100.0/24 去往HQ的流量路径
PC3 172.17.100.0/24 访问internet
AR3查看FRR
[AR3]dis ip rou vpn-instance entvpn 172.16.100.0 v Route Flags: R - relay, D - download to fib ------------------------------------------------------------------------------ Routing Table : entvpn Summary Count : 1 Destination: 172.16.100.0/24 Protocol: IBGP Process ID: 0 Preference: 255 Cost: 3 NextHop: 1.1.1.1 Neighbour: 1.1.1.5 State: Active Adv Relied Age: 00h01m41s Tag: 0 Priority: low Label: 1054 QoSInfo: 0x0 IndirectID: 0x10 RelayNextHop: 10.3.5.1 Interface: GigabitEthernet0/0/2 TunnelID: 0x1 Flags: RD BkNextHop: 1.1.1.2 BkInterface: GigabitEthernet0/0/2 BkLabel: 1053 SecTunnelID: 0x0 BkPETunnelID: 0x3 BkPESecTunnelID: 0x0 BkIndirectID: 0x14 [AR3]
4.7 Task 7: Service Deployment for Communication Between the Enterprise and Data Center Servers
4.7.1 Configuring a Virtual System on the Firewall
FW1配置vsys,服务OA server,鼠标点点也挺快
# vsys enable resource-class ent_resource resource-item-limit session reserved-number 1000 maximum 5000 resource-item-limit bandwidth 8 outbound resource-item-limit policy reserved-number 200 resource-item-limit user reserved-number 100 resource-item-limit l2tp-tunnel reserved-number 10 resource-item-limit ipsec-tunnel reserved-number 10 # # 绑定vpn-instance,重新配置IP地址 vsys name entvsys assign interface LoopBack0 assign interface GigabitEthernet1/0/1.50 assign interface GigabitEthernet1/0/1.60 assign interface GigabitEthernet1/0/2.50 assign interface GigabitEthernet1/0/2.60 assign resource-class ent_resource # firewall zone trust add interface GigabitEthernet1/0/1.50 add interface GigabitEthernet1/0/2.50 # firewall zone untrust add interface GigabitEthernet1/0/1.60 add interface GigabitEthernet1/0/2.60 #
4.7.2 Connecting the OA Server to the Network
- LSW1/LSW2配置vrf entvpn,vlanif100 划入entvpn
- vrrp配置,virtual-ip 192.168.100.1/24,LSW1 master,优先级120,抢占延迟20s
- LSW1 track G0/0/1 接口,中断后优先级减21,LSW2抢占为master
- 配置出向路由,交换机默认路由指向FW1;FW1的vsys entvsys,配置出向的主备份路由
- 配置入向路由,交换机配置指向100.1.1.10/32 的静态路由指向FW1;FW1配置去往OA192.168.100.0/24的主备路由
LSW1
# ip vpn-instance entvpn ipv4-family # interface Vlanif100 description VPN-entvpn ip binding vpn-instance entvpn ip address 192.168.100.8 255.255.255.0 vrrp vrid 1 virtual-ip 192.168.100.1 vrrp vrid 1 priority 120 vrrp vrid 1 preempt-mode timer delay 20 vrrp vrid 1 track interface GigabitEthernet0/0/1 reduced 21 # interface Vlanif50 description VPN-entvpn ip binding vpn-instance entvpn ip address 192.168.5.1 255.255.255.252 # ip route-static 100.1.1.10 255.255.255.255 100.1.6.2 ip route-static vpn-instance entvpn 0.0.0.0 0.0.0.0 192.168.5.2 #LSW2
# ip vpn-instance entvpn ipv4-family # interface Vlanif100 description VPN-entvpn ip binding vpn-instance entvpn ip address 192.168.100.9 255.255.255.0 vrrp vrid 1 virtual-ip 192.168.100.1 vrrp vrid 1 preempt-mode timer delay 20 # interface Vlanif50 description VPN-entvpn ip binding vpn-instance entvpn ip address 192.168.50.1 255.255.255.252 # ip route-static 100.1.1.10 255.255.255.255 100.1.60.2 ip route-static vpn-instance entvpn 0.0.0.0 0.0.0.0 192.168.50.2 #FW1
# switch vsys entvsys # ip route-static 0.0.0.0 0.0.0.0 100.1.6.1 ip route-static 0.0.0.0 0.0.0.0 100.1.60.1 preference 90 ip route-static 192.168.100.0 255.255.255.0 192.168.5.1 ip route-static 192.168.100.0 255.255.255.0 192.168.50.1 preference 90
4.7.3 Configuring IPsec Tunnels
- 配置172.16.100.0/24和172.17.100.0/24 走ipsec访问OA 192.168.100.0/24
- 使用IKE 协商模式
- 自动触发建立隧道
- 看图表设置参数
AR1
# bgp 64812 # ipv4-family unicast network 200.1.6.0 255.255.255.252AR2
# bgp 64812 # ipv4-family unicast network 200.1.7.0 255.255.255.252LSW1
# bgp 62022 # ipv4-family unicast network 100.1.6.0 255.255.255.252LSW2
# bgp 62022 # ipv4-family unicast network 100.1.60.0 255.255.255.252FW1
# acl number 3000 rule 5 permit ip source 192.168.100.0 0.0.0.255 destination 172.16.100.0 0.0.0.255 rule 10 permit ip source 192.168.100.0 0.0.0.255 destination 172.17.100.0 0.0.0.255 # ipsec proposal ipsec_proposal esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 10 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer fw0201 pre-shared-key Huawei@123 ike-proposal 10 remote-id-type any remote-address 200.1.6.2 ike peer fw0202 pre-shared-key Huawei@123 ike-proposal 10 remote-id-type any remote-address 200.1.7.2 # ipsec policy ipsec01 10 isakmp security acl 3000 ike-peer fw0201 proposal ipsec_proposal ipsec policy ipsec02 10 isakmp security acl 3000 ike-peer fw0202 proposal ipsec_proposal # undo policy enable # 策略禁用命令 # interface GigabitEthernet1/0/1.60 ipsec policy ipsec01 # interface GigabitEthernet1/0/2.60 ipsec policy ipsec02 # security-policy rule name ipsec_in_sp source-zone untrust destination-zone local source-address 200.1.6.0 mask 255.255.255.0 source-address 200.1.7.0 mask 255.255.255.0 action permit rule name ipsec_out_sp source-zone local destination-zone untrust destination-address 200.1.6.2 mask 255.255.255.255 destination-address 200.1.7.2 mask 255.255.255.255 action permit rule name trust2untrust source-zone trust destination-zone untrust source-address 192.168.100.0 mask 255.255.255.0 destination-address 172.16.100.0 mask 255.255.255.0 destination-address 172.17.100.0 mask 255.255.255.0 action permit rule name untrust2trust source-zone untrust destination-zone trust source-address 172.16.100.0 mask 255.255.255.0 source-address 172.17.100.0 mask 255.255.255.0 destination-address 192.168.100.0 mask 255.255.255.0 action permit #FW2
# acl number 3000 rule 5 permit ip source 172.16.100.0 0.0.0.255 destination 192.168.100.0 0.0.0.255 rule 10 permit ip source 172.17.100.0 0.0.0.255 destination 192.168.100.0 0.0.0.255 # ipsec proposal ipsec_proposal # 使用默认值,不用敲以下2行命令 esp authentication-algorithm sha2-256 esp encryption-algorithm aes-256 # ike proposal 10 # 使用默认值,不用敲以下6行命令 encryption-algorithm aes-256 dh group14 authentication-algorithm sha2-256 authentication-method pre-share integrity-algorithm hmac-sha2-256 prf hmac-sha2-256 # ike peer fw0101 pre-shared-key Huawei@123 ike-proposal 10 remote-id-type any remote-address 100.1.6.2 ike peer fw0102 pre-shared-key Huawei@123 ike-proposal 10 remote-id-type any remote-address 100.1.60.2 # ipsec policy ipsec01 10 isakmp security acl 3000 ike-peer fw0101 proposal ipsec_proposal ipsec policy ipsec02 10 isakmp security acl 3000 ike-peer fw0102 proposal ipsec_proposal # interface GigabitEthernet1/0/3.60 ipsec policy ipsec01 # interface GigabitEthernet1/0/4.70 ipsec policy ipsec02 # security-policy rule name trust2untrust01 source-zone trust destination-zone untrust source-address 172.16.100.0 mask 255.255.255.0 source-address 172.17.100.0 mask 255.255.255.0 profile ips Profile_ips_pc action permit rule name trust2untrust02 source-zone trust destination-zone untrust source-address 172.16.101.0 mask 255.255.255.0 destination-address 192.168.100.0 mask 255.255.255.0 action permit rule name ipsec_out_sp source-zone local destination-zone untrust destination-address 100.1.6.2 mask 255.255.255.255 destination-address 100.1.60.2 mask 255.255.255.255 action permit rule name ipsec_in_sp source-zone untrust destination-zone local source-address 100.1.6.2 mask 255.255.255.255 source-address 100.1.60.2 mask 255.255.255.255 action permit rule name untrust2trust source-zone untrust destination-zone trust source-address 192.168.100.0 mask 255.255.255.0 destination-address 172.16.100.0 mask 255.255.255.0 destination-address 172.17.100.0 mask 255.255.255.0 action permit #校验
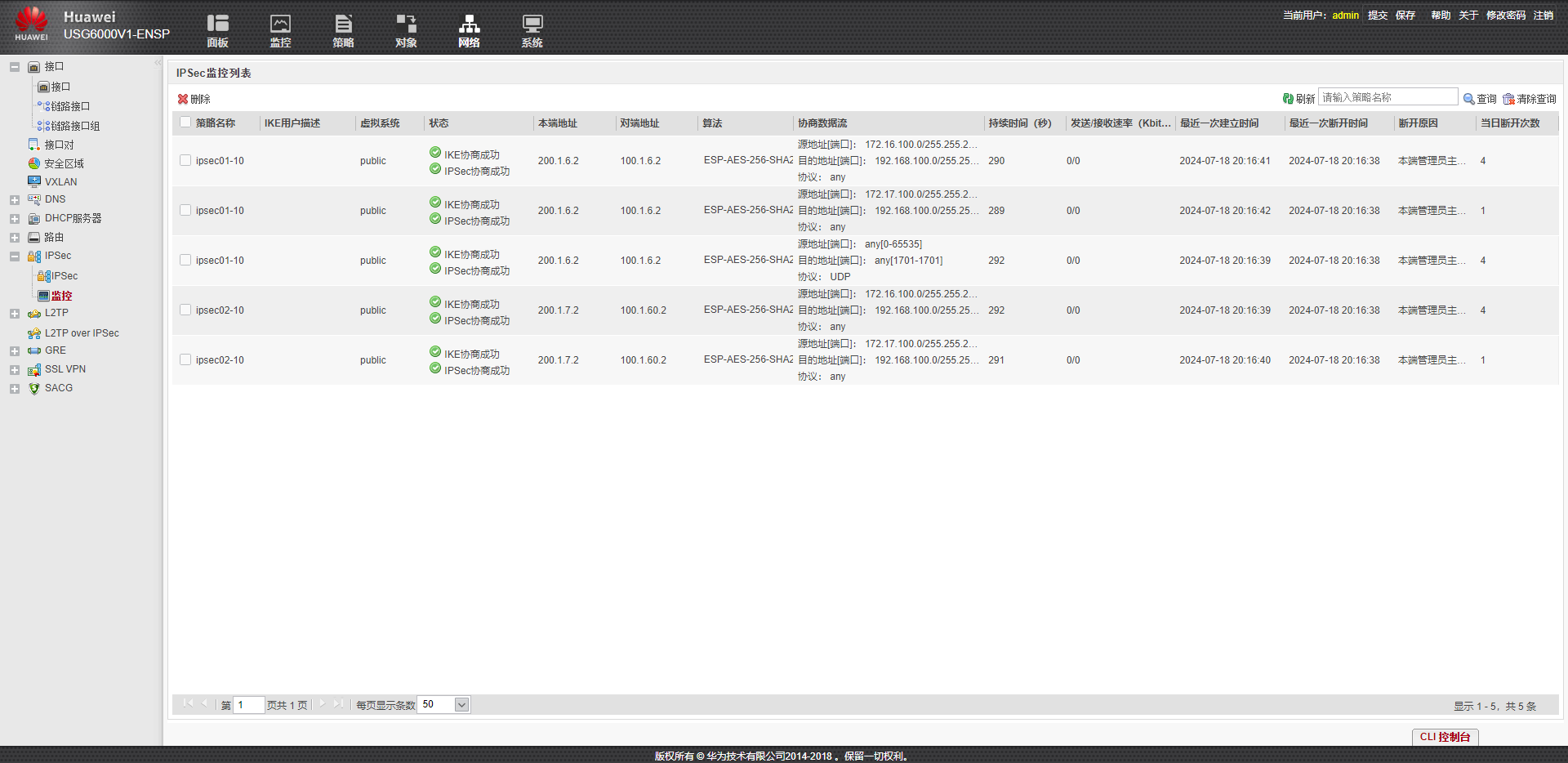
dis ipsec sa
[FW1-entvsys]dis ipsec sa 2024-07-17 09:00:34.530 ipsec sa information: =============================== Interface: GigabitEthernet1/0/1.60 =============================== ----------------------------- IPSec policy name: "ipsec01" Sequence number : 10 Acl group : 3000 Acl rule : 5 Mode : ISAKMP ----------------------------- Connection ID : 7 Encapsulation mode: Tunnel Holding time : 0d 1h 12m 55s Tunnel local : 100.1.6.2:500 Tunnel remote : 200.1.6.2:500 Flow source : 192.168.100.0/255.255.255.0 0/0-65535 Flow destination : 172.16.100.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 199477355 (0xbe3c86b) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485721/2324 Max sent sequence-number: 665 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 664/39936 [Inbound ESP SAs] SPI: 187864131 (0xb329443) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/2324 Max received sequence-number: 1 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 0/0 Anti-replay : Enable Anti-replay window size: 1024 ----------------------------- IPSec policy name: "ipsec01" Sequence number : 10 Acl group : 3000 Acl rule : 10 Mode : ISAKMP ----------------------------- Connection ID : 6 Encapsulation mode: Tunnel Holding time : 0d 0h 39m 25s Tunnel local : 100.1.6.2:500 Tunnel remote : 200.1.6.2:500 Flow source : 192.168.100.0/255.255.255.0 0/0-65535 Flow destination : 172.17.100.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 192541812 (0xb79f474) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485722/1237 Max sent sequence-number: 666 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 665/39900 [Inbound ESP SAs] SPI: 186945386 (0xb248f6a) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485754/1237 Max received sequence-number: 64 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 106/6360 Anti-replay : Enable Anti-replay window size: 1024 =============================== Interface: GigabitEthernet1/0/2.60 =============================== ----------------------------- IPSec policy name: "ipsec02" Sequence number : 10 Acl group : 3000 Acl rule : 5 Mode : ISAKMP ----------------------------- Connection ID : 8 Encapsulation mode: Tunnel Holding time : 0d 0h 53m 39s Tunnel local : 100.1.60.2:500 Tunnel remote : 200.1.7.2:500 Flow source : 192.168.100.0/255.255.255.0 0/0-65535 Flow destination : 172.16.100.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 195126685 (0xba1659d) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/3407 Max sent sequence-number: 1 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 0/0 [Inbound ESP SAs] SPI: 195412318 (0xba5c15e) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485753/3407 Max received sequence-number: 128 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 133/7980 Anti-replay : Enable Anti-replay window size: 1024 ----------------------------- IPSec policy name: "ipsec02" Sequence number : 10 Acl group : 3000 Acl rule : 10 Mode : ISAKMP ----------------------------- Connection ID : 5 Encapsulation mode: Tunnel Holding time : 0d 0h 42m 10s Tunnel local : 100.1.60.2:500 Tunnel remote : 200.1.7.2:500 Flow source : 192.168.100.0/255.255.255.0 0/0-65535 Flow destination : 172.17.100.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 184686406 (0xb021746) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/1071 Max sent sequence-number: 1 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 0/0 [Inbound ESP SAs] SPI: 187927920 (0xb338d70) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485699/1071 Max received sequence-number: 1216 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 1044/63024 Anti-replay : Enable Anti-replay window size: 1024 [FW1-entvsys]dis ipsec sa
[FW2]dis ipsec sa 2024-07-17 09:01:41.270 ipsec sa information: =============================== Interface: GigabitEthernet1/0/3.60 =============================== ----------------------------- IPSec policy name: "ipsec01" Sequence number : 10 Acl group : 3000 Acl rule : 5 Mode : ISAKMP ----------------------------- Connection ID : 47 Encapsulation mode: Tunnel Holding time : 0d 1h 14m 2s Tunnel local : 200.1.6.2:500 Tunnel remote : 100.1.6.2:500 Flow source : 172.16.100.0/255.255.255.0 0/0-65535 Flow destination : 192.168.100.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 187864131 (0xb329443) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/2257 Max sent sequence-number: 1 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 0/0 [Inbound ESP SAs] SPI: 199477355 (0xbe3c86b) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485719/2257 Max received sequence-number: 704 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 708/42576 Anti-replay : Enable Anti-replay window size: 1024 ----------------------------- IPSec policy name: "ipsec01" Sequence number : 10 Acl group : 3000 Acl rule : 10 Mode : ISAKMP ----------------------------- Connection ID : 45 Encapsulation mode: Tunnel Holding time : 0d 0h 40m 31s Tunnel local : 200.1.6.2:500 Tunnel remote : 100.1.6.2:500 Flow source : 172.17.100.0/255.255.255.0 0/0-65535 Flow destination : 192.168.100.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 186945386 (0xb248f6a) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485754/1170 Max sent sequence-number: 107 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 106/6360 [Inbound ESP SAs] SPI: 192541812 (0xb79f474) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485719/1170 Max received sequence-number: 704 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 707/42420 Anti-replay : Enable Anti-replay window size: 1024 =============================== Interface: GigabitEthernet1/0/4.70 =============================== ----------------------------- IPSec policy name: "ipsec02" Sequence number : 10 Acl group : 3000 Acl rule : 5 Mode : ISAKMP ----------------------------- Connection ID : 48 Encapsulation mode: Tunnel Holding time : 0d 0h 54m 40s Tunnel local : 200.1.7.2:500 Tunnel remote : 100.1.60.2:500 Flow source : 172.16.100.0/255.255.255.0 0/0-65535 Flow destination : 192.168.100.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 195412318 (0xba5c15e) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485750/3347 Max sent sequence-number: 178 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 177/10620 [Inbound ESP SAs] SPI: 195126685 (0xba1659d) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/3347 Max received sequence-number: 1 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 0/0 Anti-replay : Enable Anti-replay window size: 1024 ----------------------------- IPSec policy name: "ipsec02" Sequence number : 10 Acl group : 3000 Acl rule : 10 Mode : ISAKMP ----------------------------- Connection ID : 44 Encapsulation mode: Tunnel Holding time : 0d 0h 43m 11s Tunnel local : 200.1.7.2:500 Tunnel remote : 100.1.60.2:500 Flow source : 172.17.100.0/255.255.255.0 0/0-65535 Flow destination : 192.168.100.0/255.255.255.0 0/0-65535 [Outbound ESP SAs] SPI: 187927920 (0xb338d70) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485683/1011 Max sent sequence-number: 1317 UDP encapsulation used for NAT traversal: N SA encrypted packets (number/bytes): 1316/79344 [Inbound ESP SAs] SPI: 184686406 (0xb021746) Proposal: ESP-ENCRYPT-AES-256 ESP-AUTH-SHA2-256-128 SA remaining key duration (kilobytes/sec): 10485760/1011 Max received sequence-number: 1 UDP encapsulation used for NAT traversal: N SA decrypted packets (number/bytes): 0/0 Anti-replay : Enable Anti-replay window size: 1024 [FW2]PC1 ping OA
PC3 ping OA
4.7.4 Configuring an L2TP over IPsec Tunnel
- 配置l2tp over ipsec
FW1
# 切换虚拟系统,以下配置都在entvsys下配置 switch vsys entvsys # 创建user001,每次启动都需要操作一次,产品手册中指示存于数据库中,而模拟器没硬盘没这货 user-manage user user0001 password Huawei@123 # interface Virtual-Template0 ppp authentication-mode chap remote address 30.30.30.2 ip address 30.30.30.1 255.255.255.252 # firewall zone dmz add interface Virtual-Template0 # l2tp enable l2tp-group 1 tunnel password cipher Huawei@123 tunnel name lns allow l2tp virtual-template 0 remote lac # acl number 3000 rule 15 permit udp source-port eq 1701 # security-policy rule name trust2dmz source-zone trust destination-zone dmz source-address 192.168.100.0 mask 255.255.255.0 destination-address 30.30.30.0 mask 255.255.255.252 action permit rule name dmz2trust source-zone dmz destination-zone trust source-address 30.30.30.0 mask 255.255.255.252 destination-address 192.168.100.0 mask 255.255.255.0 action permit rule name untrust2local source-zone untrust destination-zone local source-address 200.1.1.11 mask 255.255.255.255 destination-address 100.1.1.10 mask 255.255.255.255 action permit rule name any action permit #FW2
# l2tp enable # l2tp-group 1 tunnel password cipher Huawei@123 tunnel name lac tunnel source LoopBack0 start l2tp ip 100.1.1.10 fullusername user001 # interface Virtual-Template0 ppp authentication-mode chap ppp chap user user001 ppp chap password cipher Huawei@123 ip address ppp-negotiate call-lns local-user user001 # policy-based-route rule name l2tp 1 source-zone trust source-address 172.16.101.0 mask 255.255.255.0 destination-address 192.168.100.0 mask 255.255.255.0 action pbr egress-interface Virtual-Template0 # nat-policy rule name l2tp source-zone trust egress-interface Virtual-Template0 source-address 172.16.101.0 mask 255.255.255.0 destination-address 192.168.100.0 mask 255.255.255.0 action source-nat easy-ip # acl number 3000 rule 15 permit udp destination-port eq 1701 # security-policy rule name trust2dmz source-zone trust destination-zone dmz source-address 172.16.101.0 mask 255.255.255.0 destination-address 192.168.100.0 mask 255.255.255.0 action permit rule name dmz2trust source-zone dmz destination-zone trust source-address 30.30.30.2 mask 255.255.255.255 destination-address 172.16.101.0 mask 255.255.255.0 action permit rule name local2untrust source-zone local destination-zone untrust source-address 200.1.1.11 mask 255.255.255.255 destination-address 100.1.1.10 mask 255.255.255.255 action permit #验证
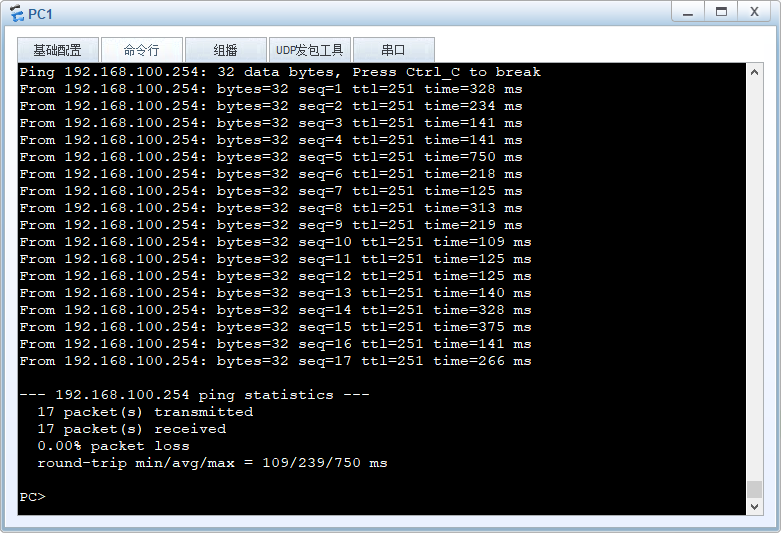
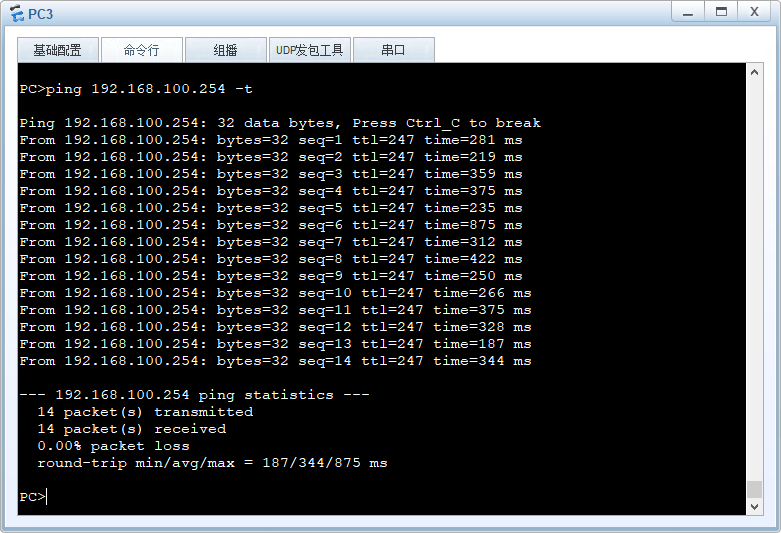
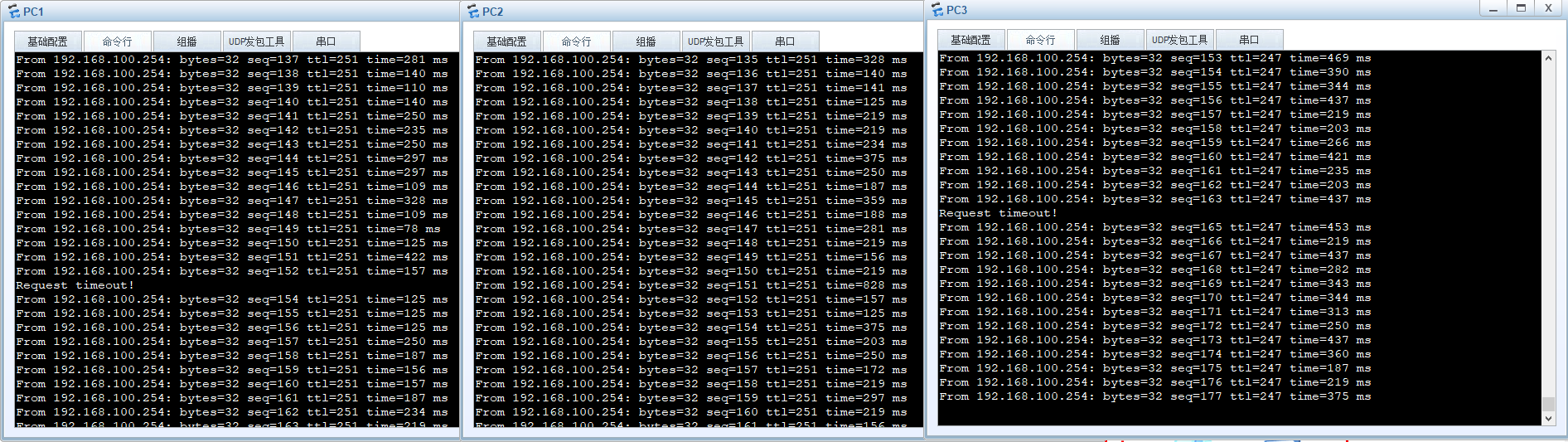
PC1 PC2 PC3 ping OA 192.168.100.254
FW2查看l2tp隧道
[FW2]dis l2tp tunnel 2024-07-18 20:01:48.860 L2TP::Total Tunnel: 1 LocalTID RemoteTID RemoteAddress Port Sessions RemoteName VpnInstance ------------------------------------------------------------------------------ 1 1 100.1.1.10 1701 1 lns ------------------------------------------------------------------------------ Total 1, 1 printed [FW2]dis l2tp session 2024-07-18 20:01:51.360 L2TP::Total Session: 1 LocalSID RemoteSID LocalTID RemoteTID UserID UserName VpnInstance ------------------------------------------------------------------------------ 69 41 1 1 user001 ------------------------------------------------------------------------------ Total 1, 1 printed [FW2]FW2查看加密计数
[FW2]dis ipsec statistics 2024-07-18 20:21:08.960 IPSec statistics information: Number of IPSec tunnels: 5 Number of standby IPSec tunnels: 0 the security packet statistics: input/output security packets: 5082/5457 input/output security bytes: 335843/362318 input/output dropped security packets: 4/7 the encrypt packet statistics: send chip: 5457, recv chip: 5457, send err: 2 local cpu: 5457, other cpu: 0, recv other cpu: 0 intact packet: 5457, first slice: 0, after slice: 0 the decrypt packet statistics: send chip: 5082, recv chip: 5082, send err: 0 local cpu: 5082, other cpu: 0, recv other cpu: 0 reass first slice: 0, after slice: 0 dropped security packet detail: can not find SA: 0, wrong SA: 0 authentication: 0, replay: 0 front recheck: 0, after recheck: 4 change cpu enc: 0, dec change cpu: 0 fib search: 0, output l3: 2 flow err: 5, slice err: 0, byte limit: 0 slave drop: 0 negotiate about packet statistics: IKE fwd packet ok: 46, err: 0 IKE ctrl packet inbound ok: 46, outbound ok: 68 SoftExpr: 0, HardExpr: 0, DPDOper: 0 trigger ok: 29, switch sa: 12, sync sa: 0 recv IKE nat keepalive: 0, IKE input: 0 [FW2]FW查看ipsec状态
4.8 Task 8: Multicast Service Deployment on the MAN
4.8.1 Configuring the Multicast Service
- 配置MAN网络的组播网络,AR4 igmpv2,
- CR1/CR2的loopback0接口选举bsr,配置优先级确保CR1成为bsr
- 配置anycast RP,创建loopback10 0100.100.100./32,loopback10地址为c-rp
- 配置msdp组播源发现协议
- AR4的g0/0/01.100,限制组播地址
- igmp加速离组
AR1
# multicast routing-enable # interface GigabitEthernet0/0/0 pim sm # interface GigabitEthernet0/0/1 pim sm #AR2
# multicast routing-enable # interface GigabitEthernet0/0/0 pim sm # interface GigabitEthernet0/0/1 pim sm #AR3
# multicast routing-enable # interface GigabitEthernet0/0/0 pim sm # interface GigabitEthernet0/0/2 pim sm #AR4
# multicast routing-enable # interface GigabitEthernet0/0/0 pim sm # interface GigabitEthernet0/0/2 pim sm # acl number 2000 rule 5 permit source 224.1.1.0 0.0.0.255 # interface GigabitEthernet0/0/1.100 pim sm igmp enable igmp group-policy 2000 2 igmp prompt-leave group-policy 2000 #CR1
# multicast routing-enable # interface GigabitEthernet0/0/0 pim sm # interface GigabitEthernet0/0/1 pim sm # interface GigabitEthernet0/0/2 pim sm # interface Ethernet1/0/1 pim sm # interface LoopBack0 pim sm # interface LoopBack10 ip address 100.100.100.100 255.255.255.255 pim sm # bgp 64812 # ipv4-family unicast network 100.100.100.100 255.255.255.255 # pim c-bsr hash-length 0 c-bsr priority 255 c-bsr LoopBack0 c-rp LoopBack10 # msdp originating-rp LoopBack0 peer 1.1.1.6 connect-interface LoopBack0 #CR2
# multicast routing-enable # interface GigabitEthernet0/0/0 pim sm # interface GigabitEthernet0/0/1 pim sm # interface GigabitEthernet0/0/2 pim sm # interface LoopBack0 pim sm # interface LoopBack10 ip address 100.100.100.100 255.255.255.255 pim sm # bgp 64812 # ipv4-family unicast network 100.100.100.100 255.255.255.255 # pim c-bsr hash-length 0 c-bsr LoopBack0 c-rp LoopBack10 # msdp originating-rp LoopBack0 peer 1.1.1.5 connect-interface LoopBack0 #验证
dis pim rp-info
[AR4]dis pim bsr-info VPN-Instance: public net Elected AdminScoped BSR Count: 0 Elected BSR Address: 1.1.1.5 Priority: 255 Hash mask length: 0 State: Accept Preferred Scope: Not scoped Uptime: 00:00:50 Expires: 00:01:20 C-RP Count: 1 [AR4] [AR4]dis pim rp-info VPN-Instance: public net PIM-SM BSR RP Number:1 Group/MaskLen: 224.0.0.0/4 RP: 100.100.100.100 Priority: 0 Uptime: 00:00:56 Expires: 00:01:34 [AR4]dis pim routing-table
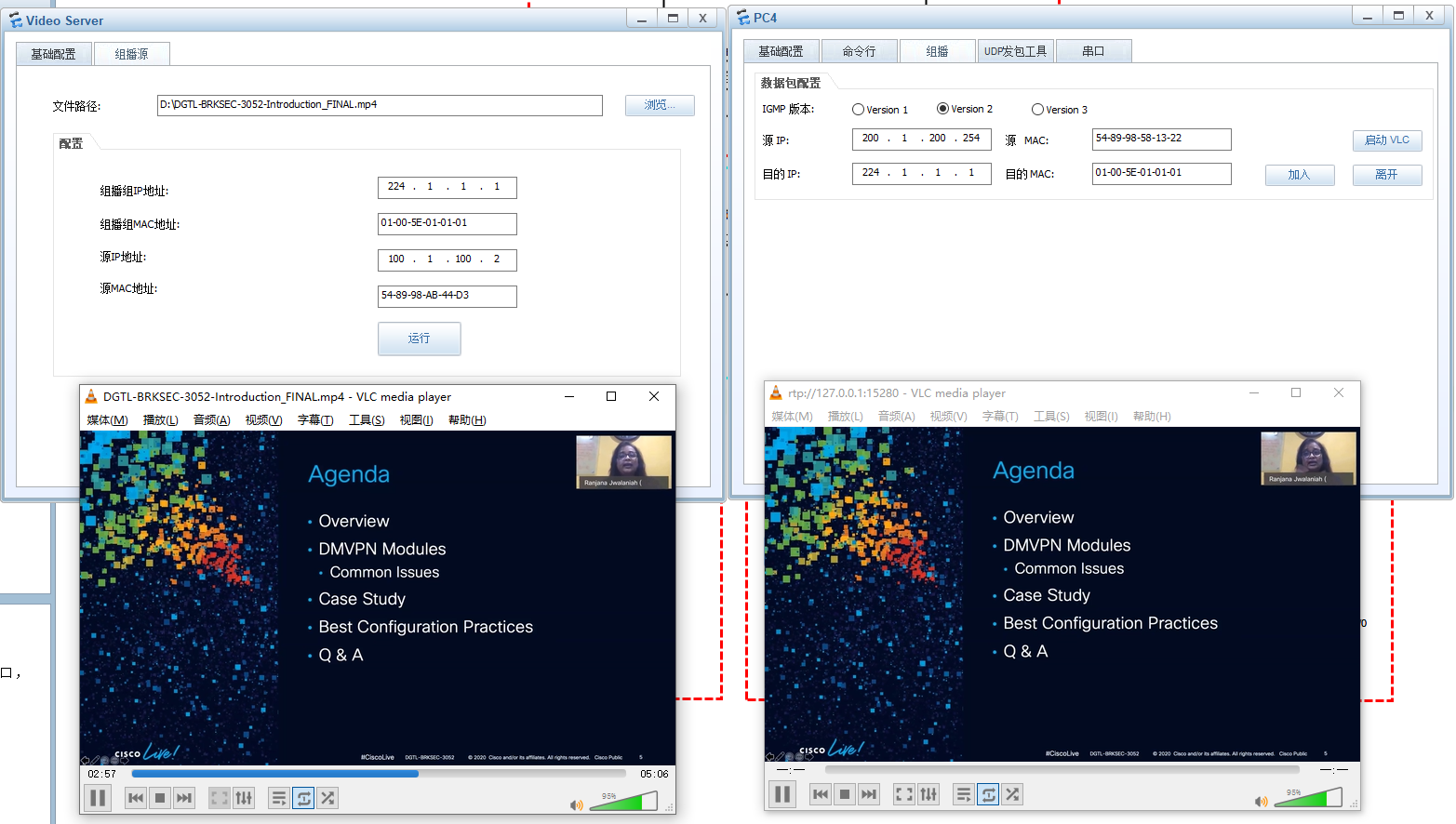
[CR1]dis pim routing-table VPN-Instance: public net Total 0 (*, G) entry; 1 (S, G) entry (100.1.100.2, 224.1.1.1) RP: 100.100.100.100 (local) Protocol: pim-sm, Flag: SPT 2MSDP LOC ACT UpTime: 00:03:16 Upstream interface: Ethernet1/0/1 Upstream neighbor: NULL RPF prime neighbor: NULL Downstream interface(s) information: Total number of downstreams: 1 1: GigabitEthernet0/0/0 Protocol: pim-sm, UpTime: 00:03:16, Expires: 00:03:14 [CR1] [CR2]dis pim routing-table VPN-Instance: public net Total 1 (*, G) entry; 1 (S, G) entry (*, 224.1.1.1) RP: 100.100.100.100 (local) Protocol: pim-sm, Flag: WC UpTime: 00:17:28 Upstream interface: Register Upstream neighbor: NULL RPF prime neighbor: NULL Downstream interface(s) information: Total number of downstreams: 1 1: GigabitEthernet0/0/2 Protocol: pim-sm, UpTime: 00:17:28, Expires: 00:03:02 (100.1.100.2, 224.1.1.1) RP: 100.100.100.100 (local) Protocol: pim-sm, Flag: SPT MSDP ACT UpTime: 00:03:41 Upstream interface: GigabitEthernet0/0/0 Upstream neighbor: 10.5.6.1 RPF prime neighbor: 10.5.6.1 Downstream interface(s) information: Total number of downstreams: 1 1: GigabitEthernet0/0/2 Protocol: pim-sm, UpTime: 00:03:41, Expires: 00:02:49 [CR2] [AR4]dis pim routing-table VPN-Instance: public net Total 1 (*, G) entry; 1 (S, G) entry (*, 224.1.1.1) RP: 100.100.100.100 Protocol: pim-sm, Flag: WC UpTime: 00:17:42 Upstream interface: GigabitEthernet0/0/2 Upstream neighbor: 10.4.6.1 RPF prime neighbor: 10.4.6.1 Downstream interface(s) information: Total number of downstreams: 1 1: GigabitEthernet0/0/1.100 Protocol: igmp, UpTime: 00:17:42, Expires: - (100.1.100.2, 224.1.1.1) RP: 100.100.100.100 Protocol: pim-sm, Flag: SPT ACT UpTime: 00:03:55 Upstream interface: GigabitEthernet0/0/2 Upstream neighbor: 10.4.6.1 RPF prime neighbor: 10.4.6.1 Downstream interface(s) information: Total number of downstreams: 1 1: GigabitEthernet0/0/1.100 Protocol: pim-sm, UpTime: 00:03:55, Expires: - [AR4]电脑安装vlc,ensp选择vlc安装路径,启动组播源服务器和PC4接收视频
最后
- 个人觉得整个拓扑的配置项还是挺多的,涉及的协议、框架、模型也挺多,有一定挑战
- 现场8个小时给我整,我是整不出来,在没有做充足准备的前提下
- 毕竟是实验,没有整防火墙双机热备
- 毕竟是实验,RR还能跑数据和接入EBGP对等体
- 毕竟是实验,AC与AC之间没有物理连线做状态监测
- 毕竟是实验,单线路多逻辑互联
- ……
- 可能有更好的实现需求的配置答案(山外有山)
- 文件存阿里云盘了,这是链接:[分享的文件 ]
- 欢迎“
来电”来函探讨。