上一篇文整了个大阵仗(内容太多,浏览器好像有些受不了)
经过在搜索引擎遨游,最终发现这些题其实在华为的ICT学院课程网站上有
https://talent.shixizhi.huawei.com –» 搜索ICT –» 华为ICT大赛 - 网络赛道学习空间(中国区)
还有其他内容,有兴趣可以点击看看
本次研究研究,搓一搓的图如标题所示
文章末尾,附上ensp拓扑文件和配置导出文件
说明
- ensp版本:1.3.00.100 V100R003C00SPC100
- 电脑:Win10 ltsc (CPU:不配拥有名称,RAM=16GB)
- 我电脑跑这图是真的卡
- 遇到FW启动错误代码40,建议先启动FW,再启动其他设备
- AR路由器我整不出G0/0/3接口,使用G3/0/0代替
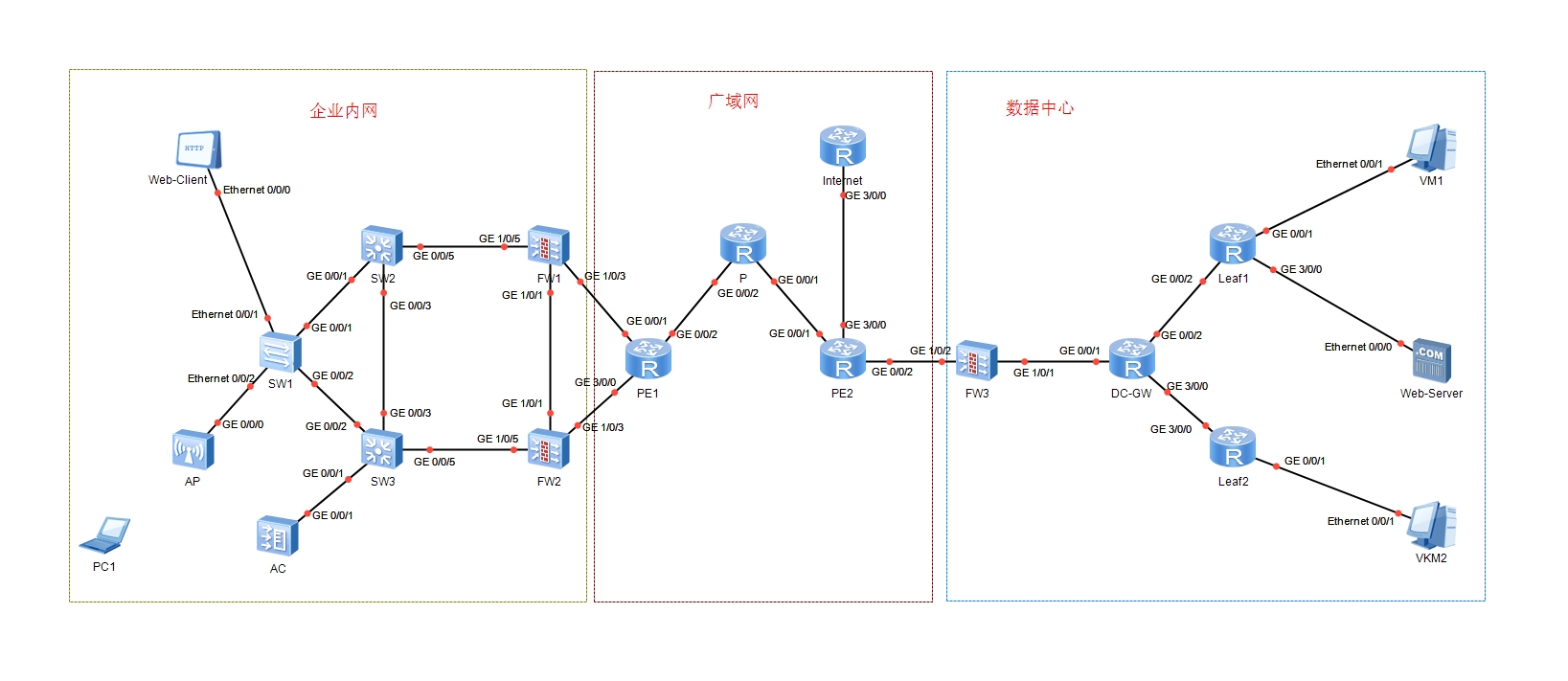
实验拓扑
配置
任务1:VLAN
- 按照给出的表格数据配置对应设备的vlan、Trunk、Access
- 路由器接口注意配置子接口dot1q termination vid xx ,arp broadcast enable
- 防火墙接口注意配置 vlan-type dot1q xx
任务2:IP地址
- 按照给出的表格数据配置对应设备的IP地址
任务3:MSTP配置
SW1
# stp mode mstp # stp region-configuration region-name RG1 instance 1 vlan 2 to 9 instance 2 vlan 10 to 20 active region-configuration # interface Ethernet0/0/1 stp edged-port enable # interface Ethernet0/0/2 stp edged-port enable #SW2
# stp mode mstp # stp region-configuration region-name RG1 instance 1 vlan 2 to 9 instance 2 vlan 10 to 20 active region-configuration # stp instance 1 priority 0 stp instance 2 priority 4096 # interface GigabitEthernet0/0/1 stp root-protection # interface GigabitEthernet0/0/5 stp disable #SW3
# stp mode mstp # stp region-configuration region-name RG1 instance 1 vlan 2 to 9 instance 2 vlan 10 to 20 active region-configuration # stp instance 1 priority 4096 stp instance 2 priority 0 # interface GigabitEthernet0/0/1 stp edged-port enable # interface GigabitEthernet0/0/2 stp root-protection # interface GigabitEthernet0/0/5 stp disable #验证: dis stp
任务4:防火墙安全域配置
FW1
# firewall zone trust add interface GigabitEthernet1/0/5.1 add interface GigabitEthernet1/0/5.2 # firewall zone untrust add interface GigabitEthernet1/0/3 add interface GigabitEthernet1/0/3.1 # firewall zone dmz add interface GigabitEthernet1/0/1 #FW2
# firewall zone trust add interface GigabitEthernet1/0/5.1 add interface GigabitEthernet1/0/5.2 # firewall zone untrust add interface GigabitEthernet1/0/3 add interface GigabitEthernet1/0/3.1 # firewall zone dmz add interface GigabitEthernet1/0/1 #FW3
# firewall zone trust add interface GigabitEthernet1/0/1 # firewall zone untrust add interface GigabitEthernet1/0/2 #验证:dis zone interface
任务5:防火墙VRRP、双机热备和安全策略配置
FW1
# interface GigabitEthernet1/0/5.1 vrrp vrid 1 virtual-ip 192.168.1.254 active # interface GigabitEthernet1/0/5.2 vrrp vrid 2 virtual-ip 192.168.2.254 standby # hrp enable hrp interface GigabitEthernet1/0/1 remote 15.1.1.2 hrp mirror session enable # security-policy rule name web source-zone trust destination-zone untrust source-address 192.168.1.0 mask 255.255.255.0 destination-address 100.1.1.1 mask 255.255.255.255 service protocol tcp destination-port 8080 action permit rule name Wireless source-zone trust destination-zone untrust source-address 192.168.2.0 mask 255.255.255.0 action permit #FW2
# interface GigabitEthernet1/0/5.1 vrrp vrid 1 virtual-ip 192.168.1.254 standby # interface GigabitEthernet1/0/5.2 vrrp vrid 2 virtual-ip 192.168.2.254 active # hrp enable hrp interface GigabitEthernet1/0/1 remote 15.1.1.1 hrp mirror session enable # # 配置hrp后,安全策略配置从HRP_M[FW1]同步,不能在HRP_S[FW2]配置 #FW3
# nat server 0 protocol tcp global 100.1.1.1 8080 inside 172.16.1.1 www # security-policy rule name web source-zone untrust destination-zone trust destination-address 172.16.1.0 mask 255.255.255.0 service http action permit #验证
任务6:公网静态路由配置
FW1
ip route-static 0.0.0.0 0.0.0.0 10.2.1.2 ip route-static 100.1.1.1 255.255.255.255 10.2.2.2FW2
ip route-static 0.0.0.0 0.0.0.0 10.3.1.2 ip route-static 100.1.1.1 255.255.255.255 10.3.2.2FW3
ip route-static 0.0.0.0 0.0.0.0 20.1.3.1 ip route-static 100.1.1.1 255.255.255.255 NULL0PE1
ip route-static 192.168.2.0 255.255.255.0 10.2.1.1 ip route-static 192.168.2.0 255.255.255.0 10.3.1.1
任务7:公网动态路由配置
PE1
# isis 1 is-level level-2 network-entity 01.0000.0010.0100.1001.00 domain-authentication-mode md5 cipher ICTEXAM # interface LoopBack0 isis enable 1 # interface GigabitEthernet0/0/2 isis enable 1 # bgp 100 router-id 1.1.1.1 peer 2.2.2.2 as-number 100 peer 2.2.2.2 connect-interface LoopBack0 #PE2
# isis 1 is-level level-2 network-entity 01.0000.0020.0200.2002.00 domain-authentication-mode md5 cipher ICTEXAM # interface LoopBack0 isis enable 1 # interface GigabitEthernet0/0/1 isis enable 1 # bgp 100 router-id 3.3.3.3 peer 2.2.2.2 as-number 100 peer 2.2.2.2 connect-interface LoopBack0 peer 20.1.4.2 as-number 200 #P
# isis 1 is-level level-2 network-entity 01.0000.0030.0300.3003.00 domain-authentication-mode md5 cipher ICTEXAM # interface LoopBack0 ip address 2.2.2.2 255.255.255.255 isis enable 1 # interface GigabitEthernet0/0/1 isis enable 1 # interface GigabitEthernet0/0/2 isis enable 1 # bgp 100 router-id 2.2.2.2 group ibgpv4 internal peer ibgpv4 connect-interface LoopBack0 peer 1.1.1.1 as-number 100 peer 1.1.1.1 group ibgpv4 peer 3.3.3.3 as-number 100 peer 3.3.3.3 group ibgpv4 # ipv4-family unicast peer ibgpv4 enable peer ibgpv4 reflect-client peer 1.1.1.1 group ibgpv4 peer 3.3.3.3 group ibgpv4 #Internet
# bgp 200 router-id 16.16.16.16 peer 20.1.4.1 as-number 100 network 16.16.16.16 255.255.255.255 #FW3
# ospf 100 default-route-advertise area 0.0.0.0 network 30.1.1.1 0.0.0.0 # interface GigabitEthernet1/0/1 ospf network-type p2p #DC-GW
# interface GigabitEthernet0/0/1 ospf network-type p2p # ospf 100 router-id 11.11.11.11 area 0.0.0.0 network 11.11.11.11 0.0.0.0 network 30.1.1.2 0.0.0.0 network 30.1.2.1 0.0.0.0 network 30.1.3.1 0.0.0.0 #Leaf1
# ospf 100 router-id 12.12.12.12 area 0.0.0.0 network 12.12.12.12 0.0.0.0 network 30.1.2.2 0.0.0.0 network 172.16.1.254 0.0.0.0 #Leaf2
# ospf 100 router-id 13.13.13.13 area 0.0.0.0 network 13.13.13.13 0.0.0.0 network 30.1.3.2 0.0.0.0 #验证
任务8:MPLS VPN
PE1
# bgp 100 # ipv4-family unicast import-route static # ipv4-family vpnv4 peer 2.2.2.2 enable # mpls lsr-id 1.1.1.1 mpls # mpls ldp # interface GigabitEthernet0/0/2 mpls mpls ldp # ip vpn-instance ToDC route-distinguisher 100:1 vpn-target 200:1 both # interface GigabitEthernet0/0/1.1 ip binding vpn-instance ToDC ip address 10.2.2.2 255.255.255.252 # interface GigabitEthernet3/0/0.1 ip binding vpn-instance ToDC ip address 10.3.2.2 255.255.255.252 # ip route-static vpn-instance ToDC 192.168.0.0 255.255.0.0 10.2.2.1 ip route-static vpn-instance ToDC 192.168.0.0 255.255.0.0 10.3.2.1 # # bgp 100 # ipv4-family vpn-instance ToDC import-route static #PE2
# bgp 100 # ipv4-family unicast peer 2.2.2.2 next-hop-local # ipv4-family vpnv4 peer 2.2.2.2 enable # mpls lsr-id 3.3.3.3 mpls # mpls ldp # interface GigabitEthernet0/0/1 mpls mpls ldp # ip vpn-instance ToDC route-distinguisher 100:1 vpn-target 200:1 both # interface GigabitEthernet0/0/2 ip binding vpn-instance ToDC ip address 20.1.3.1 255.255.255.252 # # bgp 100 # ipv4-family vpn-instance ToDC peer 20.1.3.2 as-number 300 #P
# bgp 100 # ipv4-family vpnv4 undo policy vpn-target peer ibgpv4 enable peer ibgpv4 reflect-client peer 1.1.1.1 group ibgpv4 peer 3.3.3.3 group ibgpv4 # mpls lsr-id 2.2.2.2 mpls # mpls ldp # interface GigabitEthernet0/0/1 mpls mpls ldp # interface GigabitEthernet0/0/2 mpls mpls ldp #FW3
# bgp 300 peer 20.1.3.1 as-number 100 # ipv4-family unicast import-route static #dis bgp vpnv4 all peer
dis mpls ldp int
dis mpls ldp peer
dis ip vpn-instance verbose
dis bgp vpnv4 all routing-table
任务9:GRE
Leaf1
# interface Tunnel0/0/0 ip address 173.1.2.1 255.255.255.252 tunnel-protocol gre source 12.12.12.12 destination 13.13.13.13 # ip route-static 172.16.2.0 255.255.255.0 173.1.2.2 #Leaf2
# interface Tunnel0/0/0 ip address 173.1.2.2 255.255.255.252 tunnel-protocol gre source 13.13.13.13 destination 12.12.12.12 # ip route-static 172.16.3.0 255.255.255.0 173.1.2.1 #
任务10:WLAN
FW1/FW2
# interface GigabitEthernet1/0/5.1 service-manage ping permit # interface GigabitEthernet1/0/5.2 service-manage ping permit #AC
# vlan batch 19 to 20 # dhcp enable # ip pool For_AP gateway-list 192.168.19.254 network 192.168.19.0 mask 255.255.255.0 # ip pool STA gateway-list 192.168.2.254 network 192.168.2.0 mask 255.255.255.0 excluded-ip-address 192.168.2.1 192.168.2.3 # interface Vlanif19 ip address 192.168.19.254 255.255.255.0 dhcp select global # interface Vlanif20 ip address 192.168.2.1 255.255.255.0 dhcp select global # # capwap source interface vlanif19 # wlan security-profile name s1 security wpa-wpa2 psk pass-phrase Huawei@123 aes ssid-profile name s1 ssid ICT vap-profile name p1 forward-mode tunnel service-vlan vlan-id 20 ssid-profile s1 security-profile s1 ap-group name default radio 0 vap-profile p1 wlan 1 ap-id 1 type-id 56 ap-mac 00e0-fcef-0250 ap-sn 2102354483100961AE61 ap-group default #
综合测试
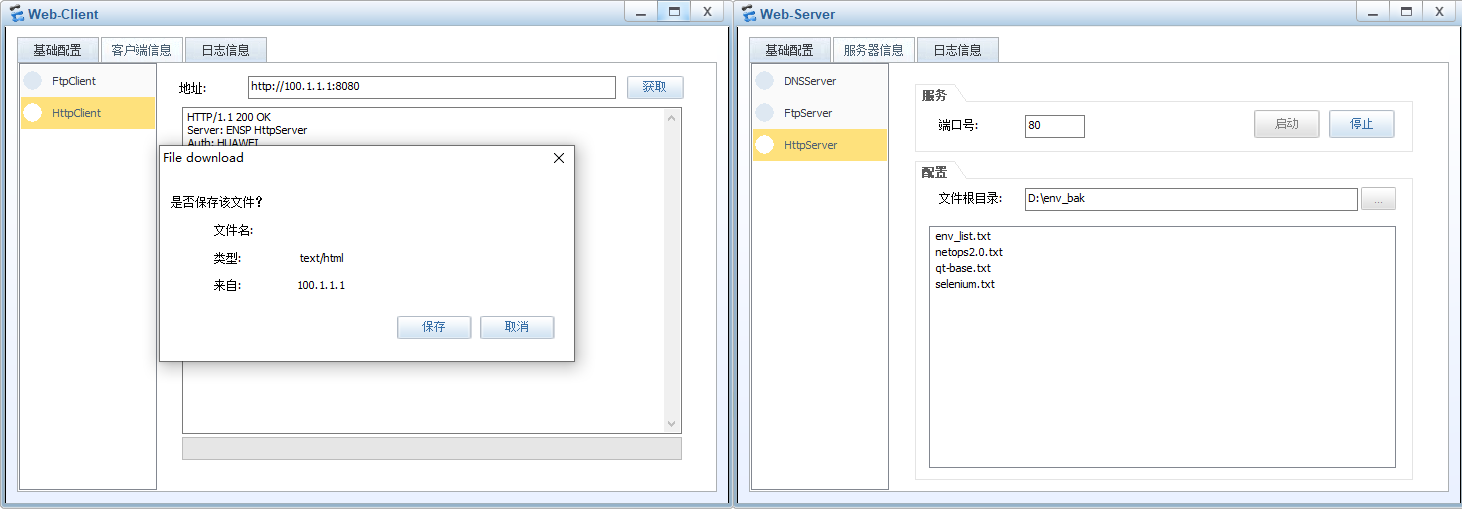
Web-Client访问Web-Server
FW3查看会话
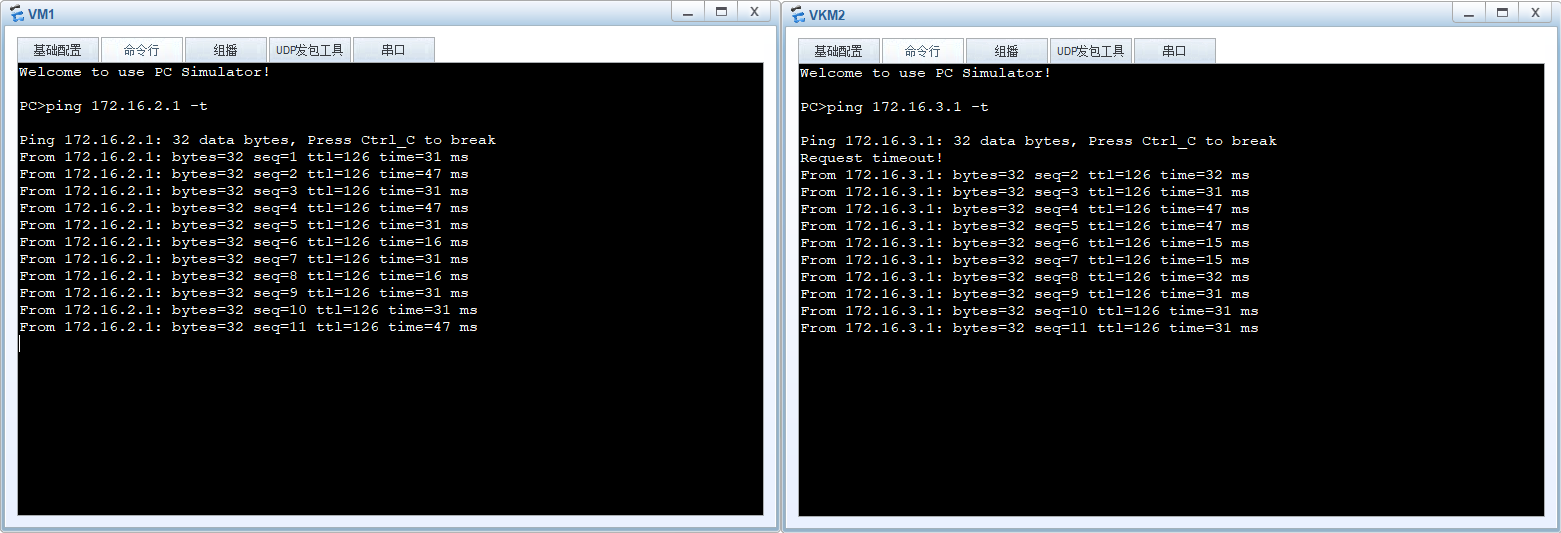
<FW3>dis firewall session table verbose 2024-07-24 03:54:01.520 Current Total Sessions : 2 http VPN: public --> public ID: c487fdedb993138324f66a07acf Zone: untrust --> trust TTL: 00:00:10 Left: 00:00:05 Recv Interface: GigabitEthernet1/0/2 Interface: GigabitEthernet1/0/1 NextHop: 30.1.1.2 MAC: 00e0-fc45-0d43 <--packets: 5 bytes: 515 --> packets: 6 bytes: 399 192.168.1.1:2050 --> 100.1.1.1:8080[172.16.1.1:80] PolicyName: web TCP State: close bgp VPN: public --> public ID: c487fdedb99d128393566a074da Zone: untrust --> local TTL: 00:20:00 Left: 00:20:00 Recv Interface: GigabitEthernet1/0/2 Interface: InLoopBack0 NextHop: 127.0.0.1 MAC: 0000-0000-0000 <--packets: 64 bytes: 3,158 --> packets: 68 bytes: 3,404 20.1.3.1:49928 --> 20.1.3.2:179 PolicyName: --- TCP State: established <FW3>VM1和VM2互相ping测试
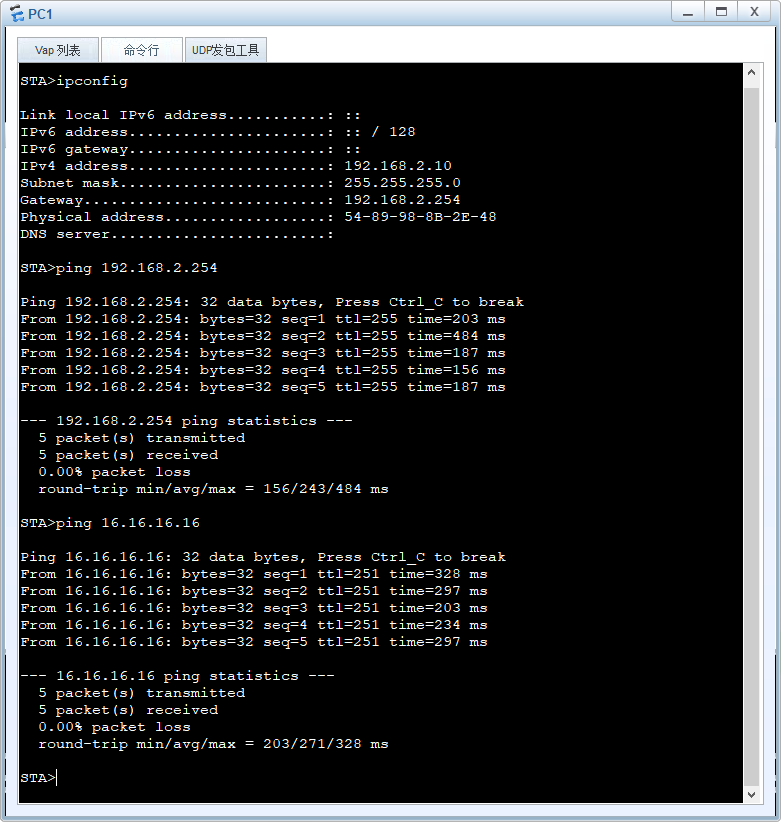
无线客户端PC1 ping测试
最后
- 个人觉得整个拓扑的就必上一篇文的规模小多了,量也没那么大,技术要点也不考察那么细致
- 貌似模拟器的USG防火墙有bug,拓扑中FW3与PE2建立EBGP,FW3与DC-GW建立OSPF,均不用配置安全策略就能建立起邻居关系
- 就不过多总结了,都在敲击键盘的过程中了
- 把文中的配置复制粘贴进对应设备最终就能实现综合测试的结果
- ……
- 可能有更好的实现需求的配置答案(山外有山)
- 文件存阿里云盘了,这是链接:[分享的文件 ]
- 欢迎“
来电”来函探讨。